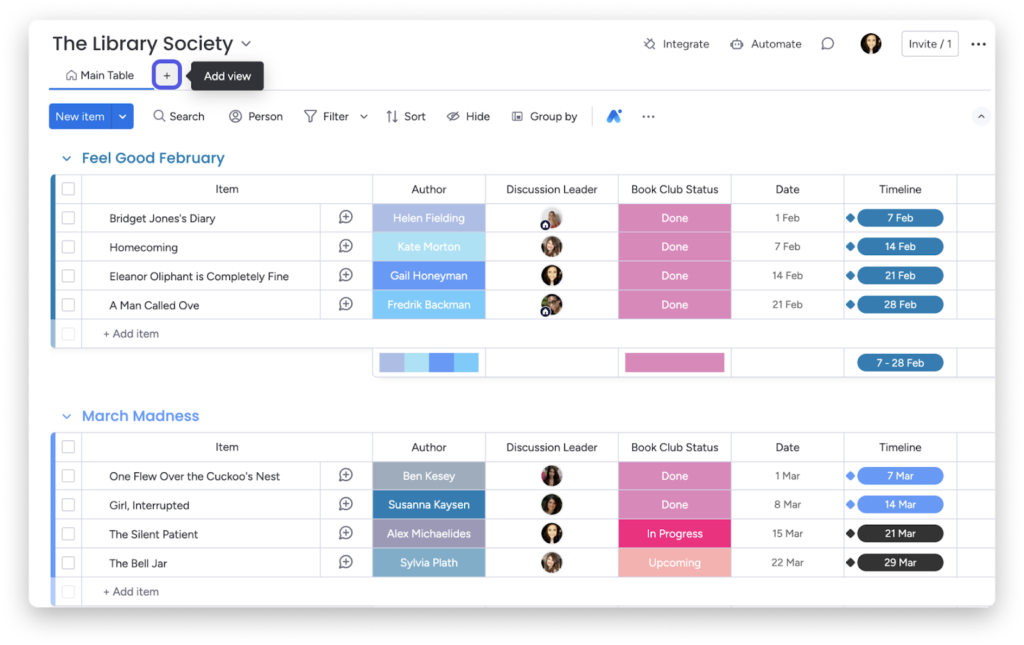
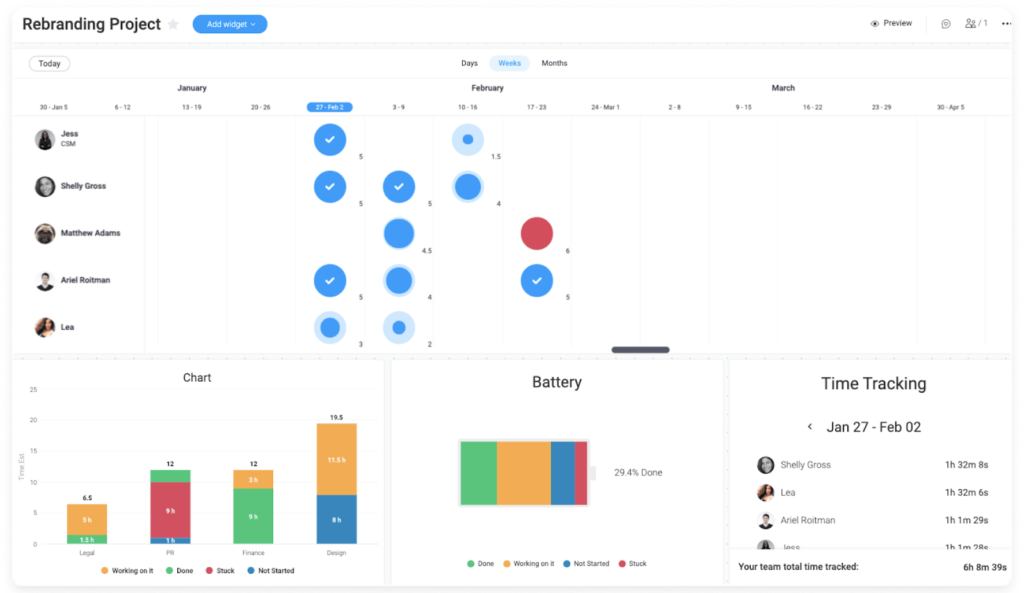
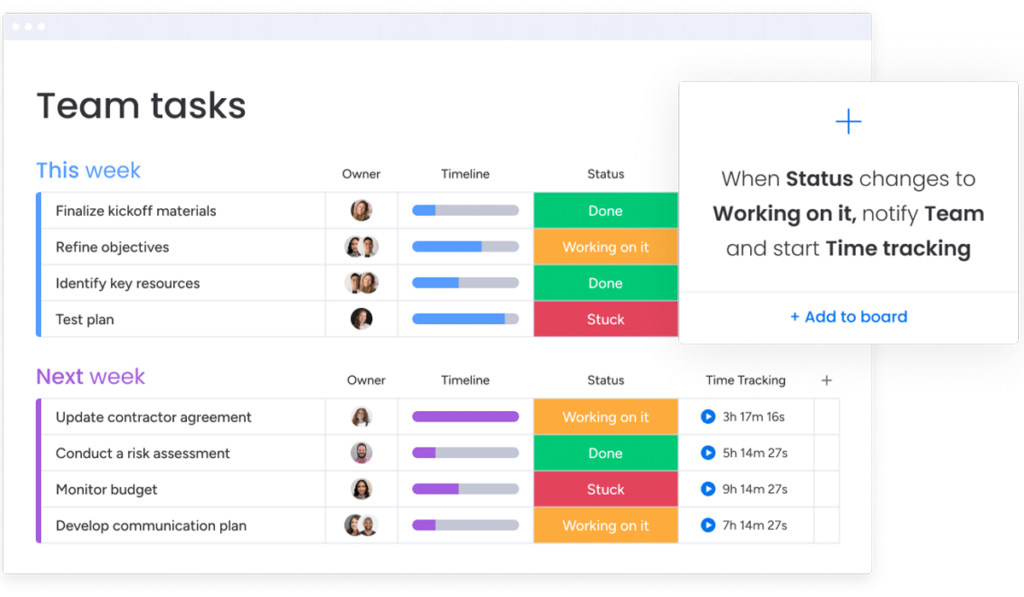
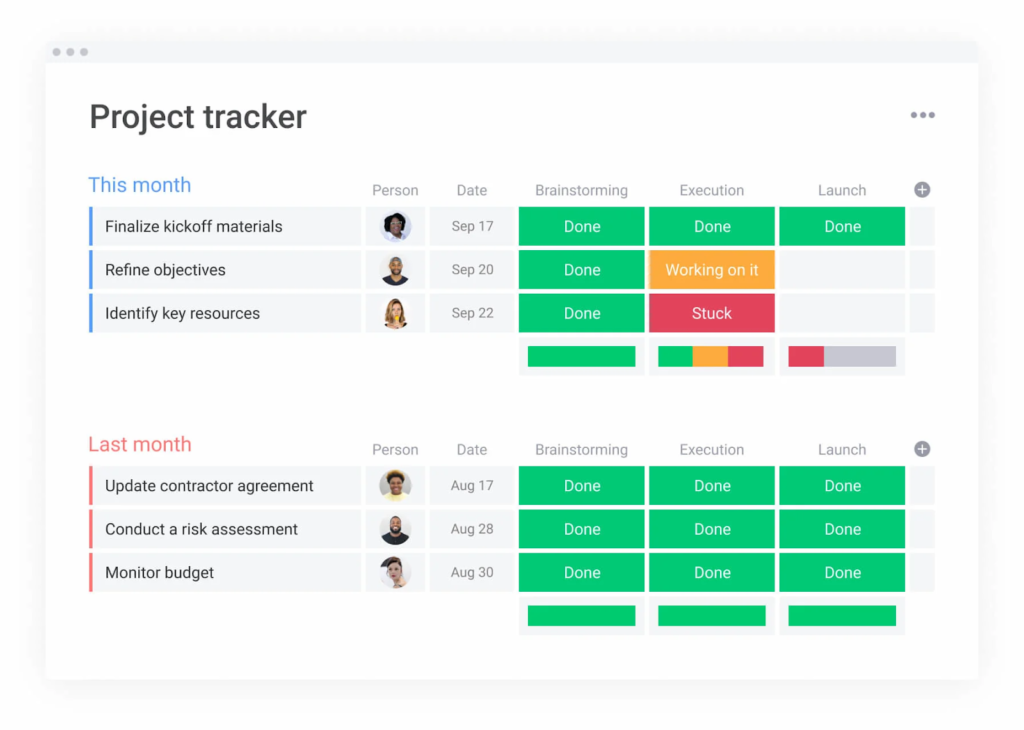
These are the 10 best project management software options for project managers of every experience level, based on our hands-on experience.
- monday work management – Best All-Around Performer
- Smartsheet – Best for Fast-Growing Teams
- Wrike – Best for Customization
- ClickUp – Best for Freelancers
- Jira – Best for Agile Teams
- Asana – Best for Remote Teams
- Trello – Best for Smaller Projects & Teams
- Notion – Best for Creative Teams
- Basecamp – Best for Collaboration
- GanttPRO – Best Option for Beginners
As always, our editorially independent picks are based on first-party research and hands-on experience of our writers and editors.
Our Picks
These are our picks for the best project management tools on the market, recently updated with current pricing and expert insights to help you choose the best project management tool for your team. We’ve also identified the key difference maker for each pick—the key aspect of each selection that make it stand out from the pack.
Let’s dive in.

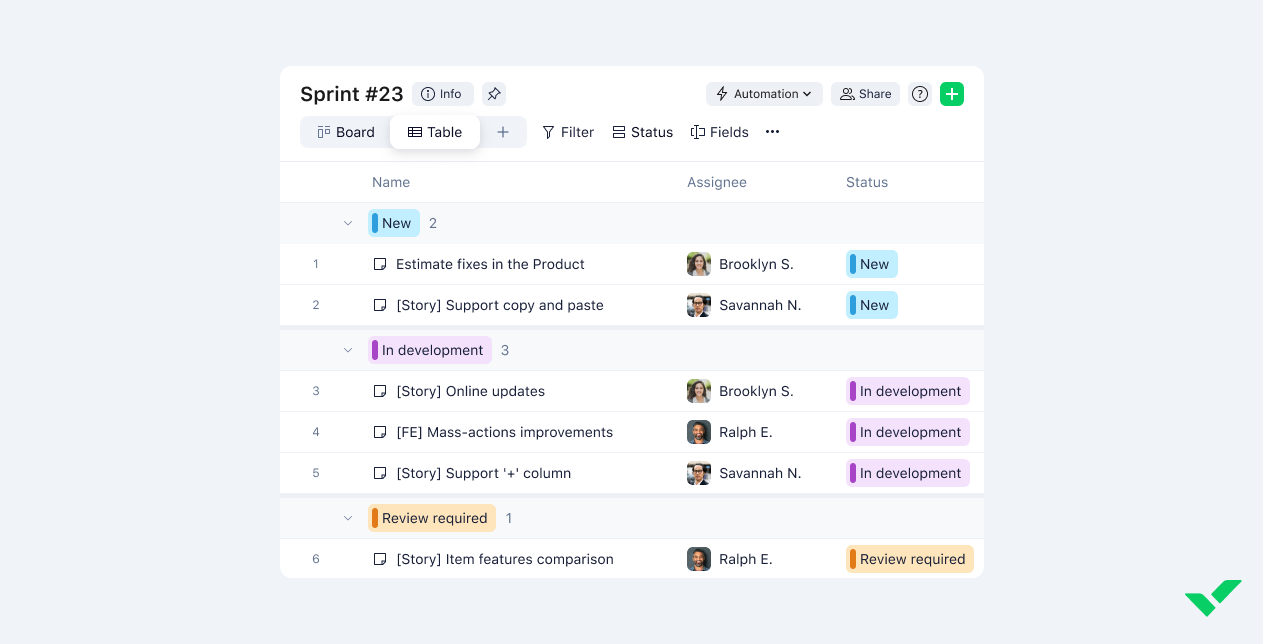
monday work management – Best all-around performer
monday work management is a cloud-based, highly customizable and visual project management tool designed to support teams of all sizes and industries. It offers an intuitive, centralized workspace with drag-and-drop functionality, automations, and real-time collaboration features to streamline workflows and boost team efficiency.
monday allows users to tailor views, build dashboards, and choose from ready-to-use templates to manage tasks, track progress, and report results effectively. The platform supports file sharing, portfolio management, calendar syncing, and integrates with email and analytics tools.
monday.com also offers a free plan for up to two users, along with tiered paid options for growing teams. It also has a mobile app for both iOS and Android devices that has all the necessary collaboration and project management features you can find in the desktop and website applications.
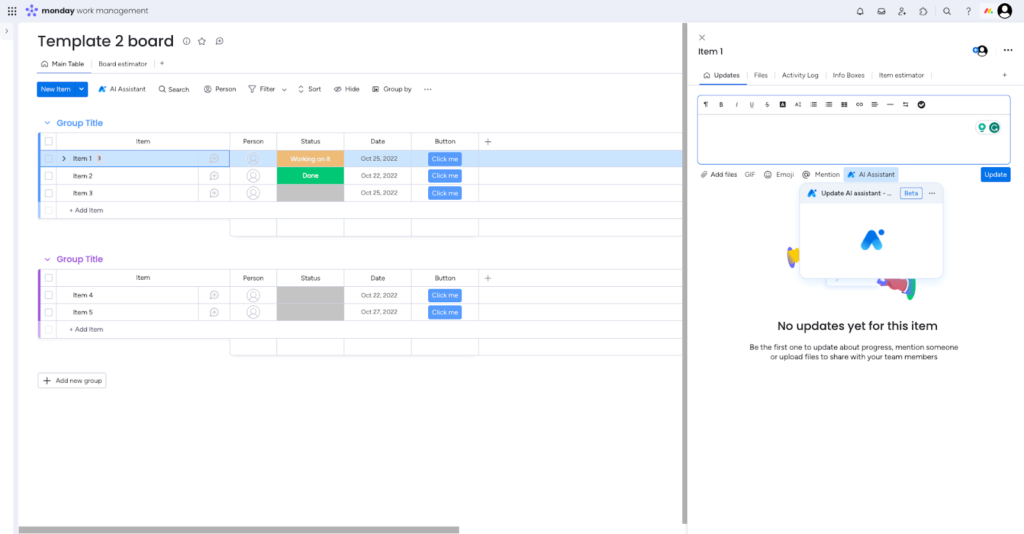
Screenshots
Standout features
- AI assistant for summarizing updates and suggesting next steps
- Custom dashboards with widgets, KPIs, and workload overviews
- Unlimited boards, file storage, and interactive docs for paid plans
- Drag-and-drop automations, conditional logic, recurring tasks
- View modes: Timeline, Kanban, Calendar, Gantt, Table, Workload
Key integrations
- Slack, Zoom, Microsoft Teams, Google Workspace, Outlook
- CRM tools like HubSpot, Salesforce
- Dev tools: GitHub, GitLab, Jira
- Automation: Zapier, Make (Integromat)
These integrations make monday ideal for cross-functional teams and multi-tool environments.
Pricing
- Free plan: Up to 2 users, basic features
- Basic: $9/user/month — for team collaboration
- Standard: $12/user/month — adds Timeline and Gantt view, integrations
- Pro: $19/user/month — adds advanced reporting, time tracking
- Enterprise: Custom — adds SSO, HIPAA, audit logs
Support
- 24/7 support on all plans (chat and email)
- Knowledge base, onboarding webinars, live training
- Excellent user community and templates
Pros
Cons
Why we picked monday work management
monday.com hits the sweet spot for most teams: it’s visually intuitive, highly flexible, and scales with you. Whether you’re managing marketing campaigns, sales pipelines, or dev sprints, monday adapts without forcing you to overhaul your workflow. Finally, it is versatile enough for marketers, devs, agencies, and enterprise teams. Its ease of use plus deep customization options earn it our top spot.
monday work management’s key differences: Focus and features
monday work management stands out because its ultimate focus is on flexibility, allowing users and their teams to take on and manage any type of work. The platform comes with customizable boards, automations, and dashboards — features that make it ideal for managing various work processes, cross-departmental workflows, and project execution.
Read our complete monday software review.

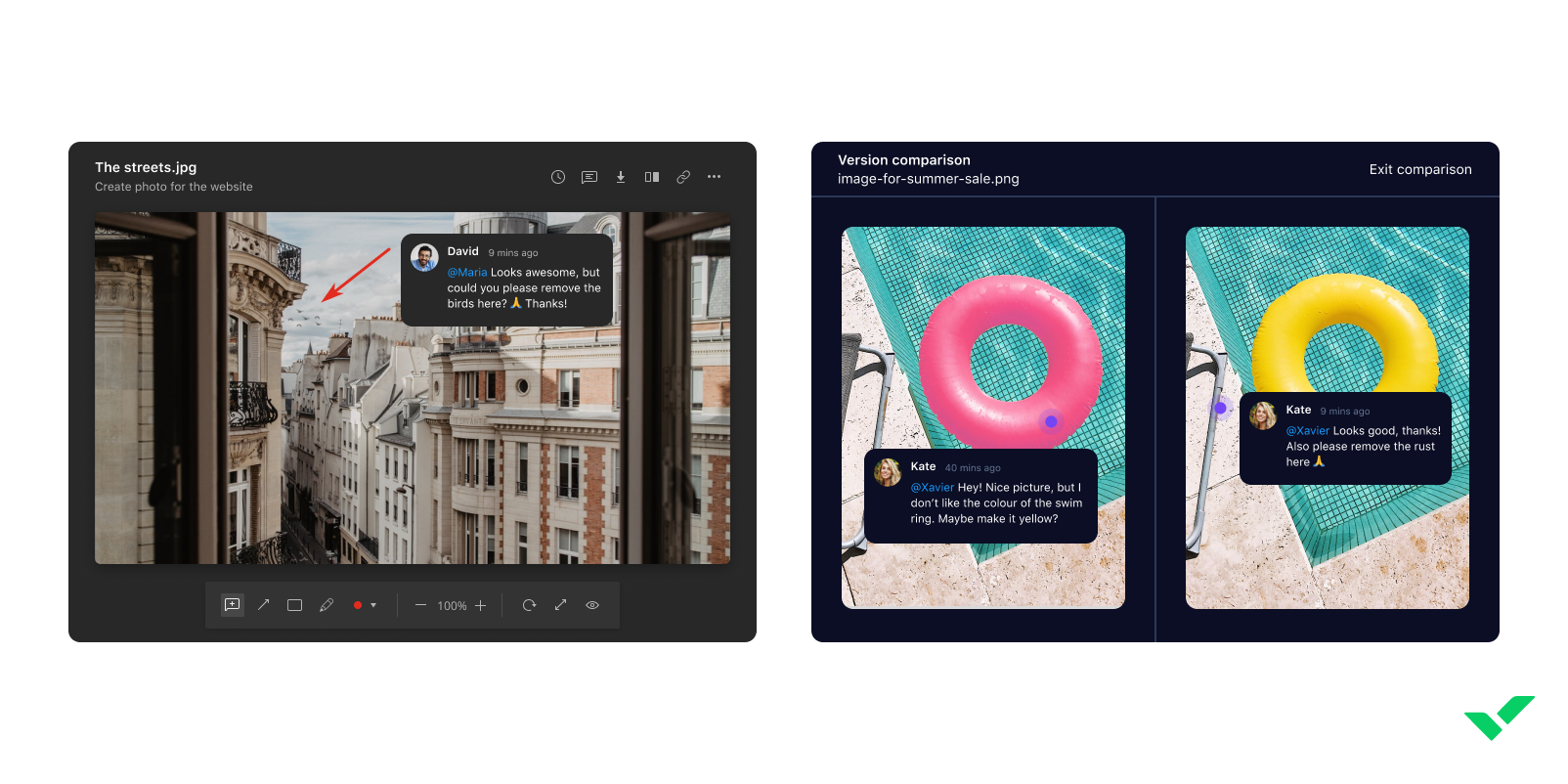
Smartsheet — Best for fast-growing teams
Smartsheet is a powerful work execution platform that enables teams to plan, execute, and report on projects in real time, making it ideal for both agile and waterfall workflows. The cloud-based software solution offers multiple project views, including Gantt, card, grid, and calendar, to support different team preferences and project types.
Key features include advanced dashboard reporting, automated update requests, and robust collaboration tools. Smartsheet also excels in resource management, offering visibility into team availability to optimize workload distribution. Its mobile app helps you keep work moving by allowing you upload photos, mark your current location, scan barcodes, as well as use offline forms so you can capture information anywhere even without internet connection.
Screenshots
Standout features
- Predicts deadlines, recommends assignees, and flags overdue work through Work Insights
- Real-time Gantt, Grid, Kanban, and Calendar views
- Cross-project dashboards and portfolio tracking
- Allows users to assign and balance workloads visually for enhanced resource management
- Formulas and functions to perform basic calculations and lookups within a single sheet or across multiple sheets
- Offers dynamic view that enables project owners to share specific data slices with clients/vendors for viewing and editing and can be accessed even by external unlicensed users
Key integrations
- Microsoft Teams, Slack, Zoom, Google Workspace
- Tableau, Power BI for external reporting
- Salesforce, HubSpot (CRM)
- Jira, GitHub (dev workflows)
These integrations make Smartsheet perfect for ops-heavy teams, PMOs, and those managing multiple tools across departments.
Pricing
- Free: 1 user, 2 editors, limited features
- Pro: $7/user/month — basic project features
- Business: $25/user/month — advanced automation, views, integrations
- Enterprise: Custom pricing — governance, control, premium support
Support
- Web-based ticketing support on all plans
- 24/7 global phone support and add-on Pro Desk guide coaching sessions on Business and Enterprise
- Extensive help center, webinars, and solution templates
Pros
Cons
Why we picked Smartsheet
We found Smartsheet to be the ideal choice for fast-scaling companies that need project structure and enterprise-grade flexibility. A spreadsheet-style interface makes it intuitive for Excel users but powerful enough for large-scale cross-functional programs. Smartsheet is built for scale. It shines in matrixed environments where reporting, visibility, and process control are essential, especially if your team is growing fast.
Smartsheet’s key differences: Flexibility and scalability
Smartsheet combines flexibility and scalability with its impressive features specifically designed for teams that need to manage work of varying complexity. Smartsheet can scale from a single project to end-to-end work management. It connects businesses on a no-code, cloud-based platform, allowing anyone to create customized solutions.
Unlike traditional tools, Smartsheet offers multiple views including Grid, Gantt, Calendar, and Kanban Card, plus timelines with dependencies, automated notifications, and Sights dashboards for portfolio visibility.
Read our complete Smartsheet software review.

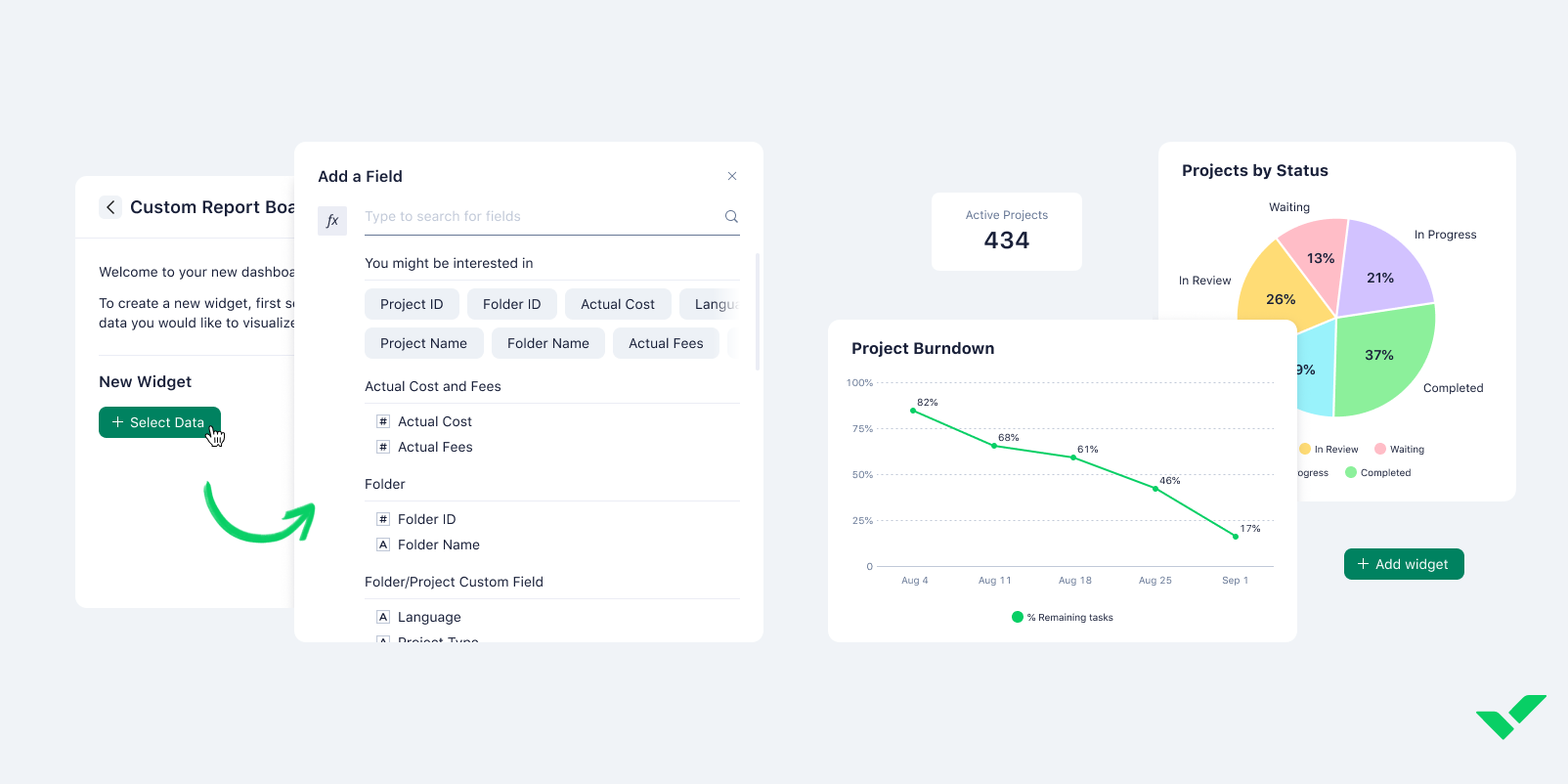
Wrike — Best for customization
Wrike is a highly flexible and powerful project management platform built to support diverse teams, from marketing and design to product management and business operations. Its adaptable interface makes it suitable for various workflows, including agile teams and remote collaboration.
Wrike’s free plan supports unlimited users for basic task management, while paid tiers unlock advanced tools like time tracking, shareable dashboards, custom workflows, and automation features. For enterprises, it offers robust security options such as SSO, 2FA, custom roles, and audit logs, which are useful for managing work across hybrid environments.
Wrike’s mobile application allows users to access their entire network environment, eliminating the need to toggle between multiple apps. Wrike Mobile has an offline mode that lets you continue to get work done without an internet connection, and when you’re back on network, Wrike automatically syncs all information so you don’t lose any important data.
Screenshots
Standout features
- New AI tools for task prioritization, summarizing projects, and general updates
- Fully customizable dashboards, workflows, and task types
- Time tracking, cross-tagging, file proofing, and request forms
- Role-based access and custom user permissions
- Interactive Gantt charts, shared calendars, workload views
Key integrations
- Slack, Microsoft Teams, Zoom for communication and collaboration
- Salesforce, HubSpot (CRM)
- Adobe Creative Cloud for marketing teams
- GitHub, GitLab, Jira for software development projects
- Google Workspace, Outlook, Box, Dropbox
These integrations power marketing operations, product dev, client service, and IT projects alike.
Pricing
- Free: Unlimited users, simple task management
- Team: $9.80/user/month — for growing teams
- Business: $24.80/user/month — full customization, automations
- Enterprise/Plus: Custom pricing — SSO, advanced security, analytics
Support
- Help center, chatbot, community forums
- Email support for all users; chat and phone for paid plans
- Dedicated customer success for Business+ and Enterprise plans
Pros
Cons
Why we picked Wrike
We picked Wrike for its ability to support teams with complex workflows or that need their project management system to adapt to very specific processes. From marketing endeavors to software development projects, the tool’s deep customization options make it versatile enough to support any industry or project structure.
Wrike is a powerhouse for teams with specific process needs, especially when cross-functional visibility, automation, and precision are top priorities. If you want deep customization, Wrike is your tool.
Wrike’s key difference: Broad view of team productivity
Wrike stands out as a project management tool due to its holistic approach to team productivity. Unlike other solutions, Wrike covers a wide spectrum of functions — from work initiation and structuring to collaboration, reporting, and integrations. It is also entirely cloud-based and can be accessed instantly by remote workers. Wrike’s versatility is what makes it ideal for larger and diverse team needs.
Wrike has features like dynamic request forms, templates, and custom item types that are the best fit for unique processes. The tool’s user-friendly dashboard, equipped with enterprise-grade tools, serves well for both one-time projects and ongoing or business-as-usual tasks.
Read our complete Wrike software review.

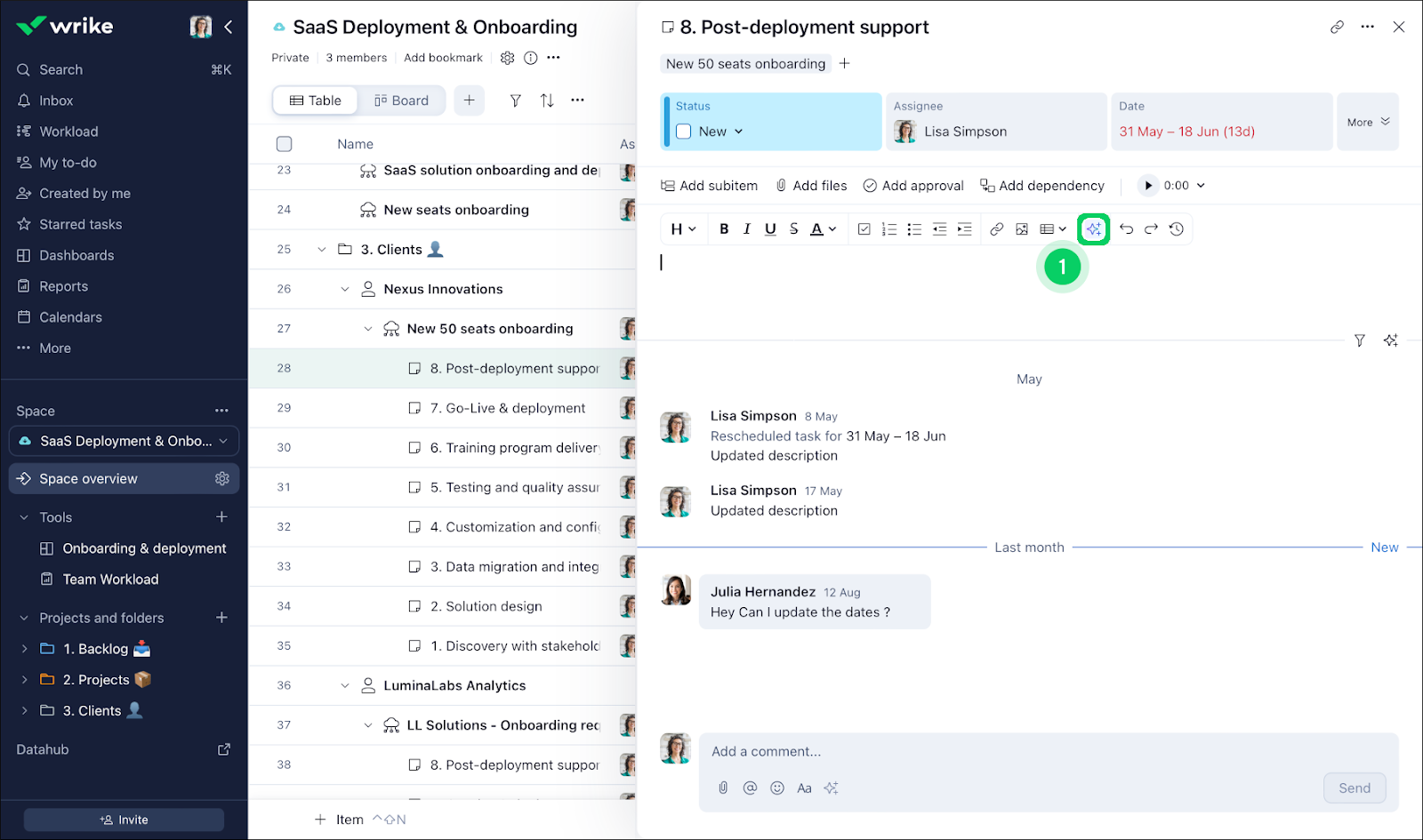
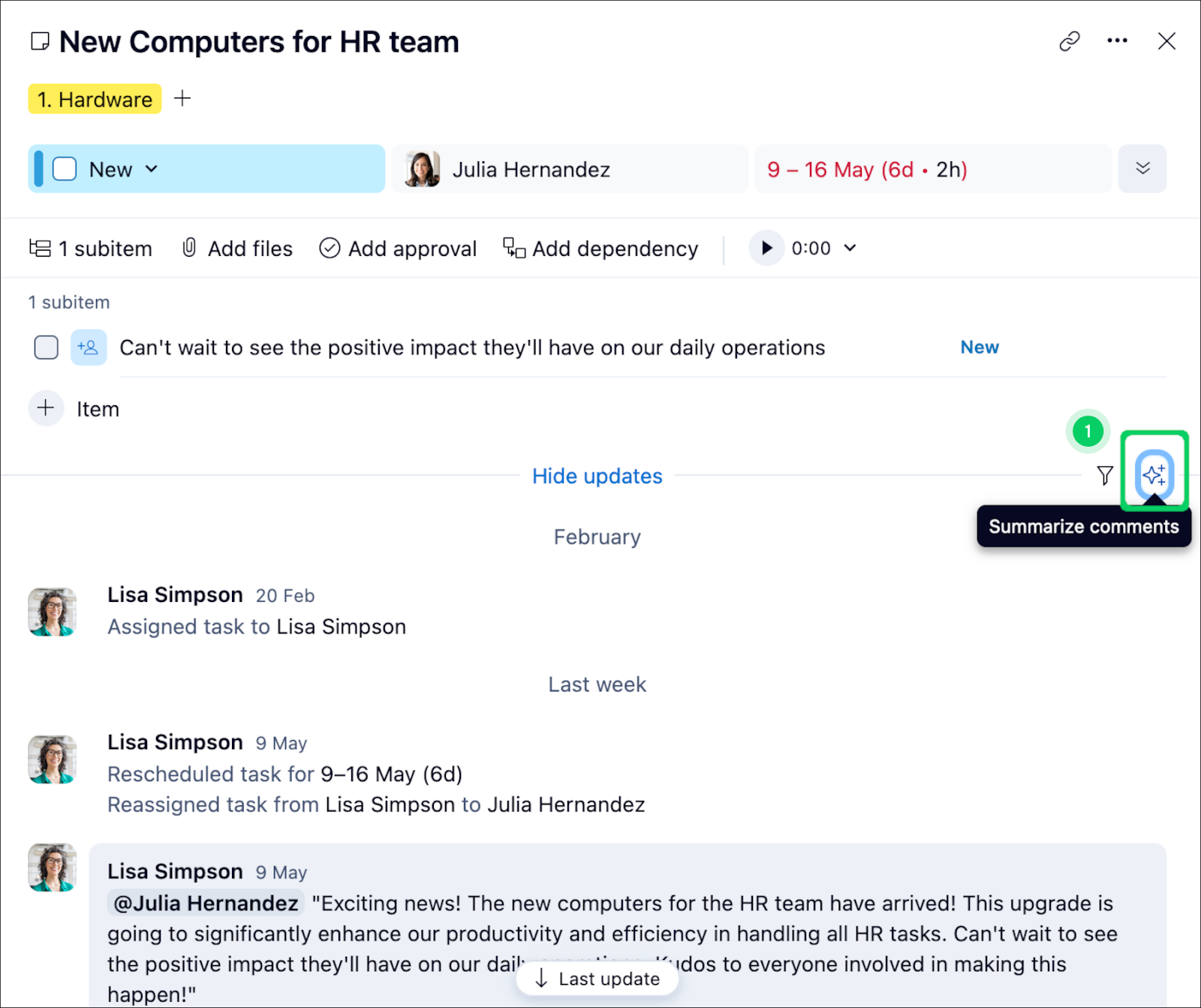
ClickUp — Best free option
ClickUp is considered one of the best project management software solutions for its generous free plan that supports unlimited users and projects. With 11 task views, customizable workflows, and newly added AI features, it’s well-suited for managing complex projects with interdependent tasks across mid- to large-sized teams.
ClickUp enables teams to handle all types of work within a single, unified platform. It also has a mobile app that offers the same level of convenience so you can stay on top of your tasks anytime, anywhere. ClickUp’s flexibility and depth make it a strong choice for growing organizations looking for a no-cost solution.
Screenshots
Standout features
- Generous free plan that includes unlimited tasks, projects, users, and multiple view types
- 15+ task views including List, Board, Calendar, Gantt, Timeline, Box, and Mind Map
- AI-powered writing, task generation, and project summaries
- Chat, docs, whiteboards, screen recordings for real-time collaboration
- Spaces, folders, lists, and tasks for improved hierarchical organization
Key integrations
- Slack, Microsoft Teams, Zoom
- Google Workspace, Outlook, Dropbox
- HubSpot, Salesforce (CRM)
- GitHub, GitLab, Bitbucket
- Zapier, Make, and native automation tools
ClickUp’s integration range makes it easy to plug into existing workflows across industries.
Pricing
- Free Forever: Unlimited users and tasks, 100 MB storage
- Unlimited: $7/user/month — adds integrations, dashboards
- Business: $12/user/month — adds timelines, workload, goals, advanced automations
- Enterprise: Custom — adds SSO, HIPAA, team sharing, white labeling
Support
- 24/7 live chat support on all paid plans
- Knowledge base, training webinars, and onboarding guides
- Community forum and help bot for free users
Pros
Cons
Why we picked ClickUp
We chose ClickUp because it offers the most generous free plan on the market — perfect for startups or solopreneurs who want powerful project tools without spending a dime. This cloud-based project management tool also scales well into larger use cases, thanks to its deep customization and new AI enhancements.
ClickUp is the ideal entry point into project management. It’s free, powerful, and feature-rich, and when your team outgrows it, you can just upgrade to a paid version and not have to completely switch tools — a smart choice for teams testing the waters or bootstrapping.
ClickUp’s key difference: Solid solution for basic project management
ClickUp’s Free Forever plan provides a solid solution for project management and a foundation for users to explore its features and decide if it’s the right choice before committing to a paid plan or exploring other options.
Learn more in our ClickUp software review.

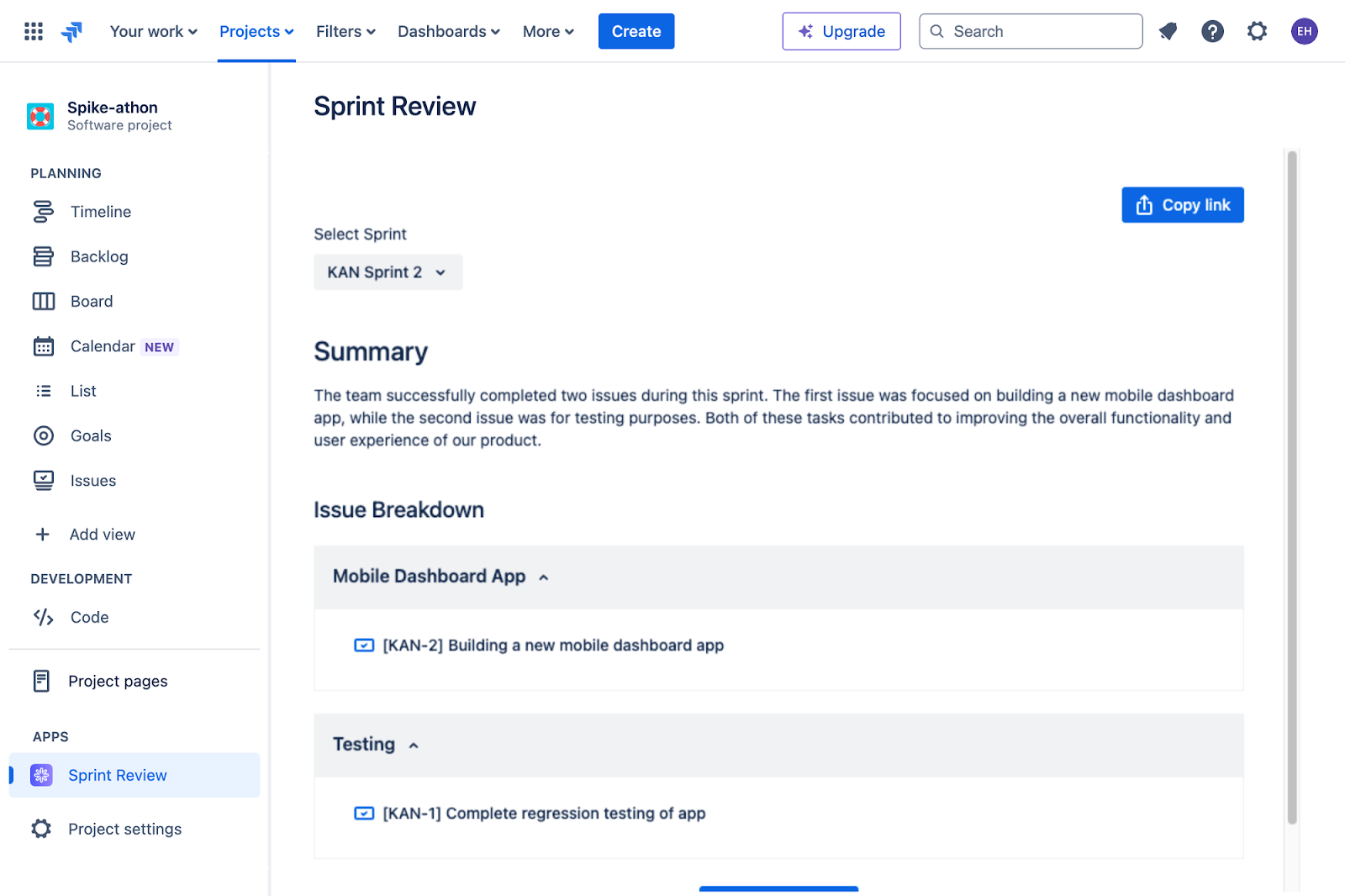
Jira — Best for agile teams
Jira, part of the Atlassian suite of cloud-based applications, is a leading project and issue-tracking tool tailored for development and technical teams. It offers powerful task management features that help users plan, track, and complete projects efficiently, including support for recurring tasks.
Jira’s free plan includes access for up to 10 users, and its scalable paid plans come with AI-powered features that help simplify setting up, tracking, and collaborating across work. It also includes multiple views, including lists, boards, timelines, and calendars, to suit different workflows. Its drag-and-drop form builder, automation rules, and vast library of integrations make it highly customizable for a wide range of project scenarios.
Jira also has mobile apps so you can respond faster and move work forward from anywhere, anytime, away from your desk. Jira’s web and mobile applications deliver the same capabilities, like issue creation, boards and backlogs, reports, and releases.
Screenshots
Standout features
- Scrum, Kanban, and hybrid agile boards
- Powerful backlog management, roadmaps, and velocity tracking
- Built-in automation rules (e.g., auto-assign, status transitions, email alerts)
- Enhanced Form Builder for standardizing tasks and issue submissions
- Smart AI features for sprint insights and project summaries
Key integrations
- Bitbucket, GitHub, GitLab — for dev workflow automation
- Confluence — for documentation and knowledge sharing
- Slack, Microsoft Teams — for team updates and alerts
- Zoom — for built-in video standups
- 3,000+ additional apps via Atlassian Marketplace (including CRM tools)
These integrations create a seamless Agile ecosystem for development-focused teams.
Pricing
- Free: Up to 10 users — basic agile boards and backlog
- Standard: $8.15/user/month — project roles, audit logs
- Premium: $16.15/user/month — advanced roadmaps, sandbox
- Enterprise: Custom — unlimited instances, SAML SSO, 24/7 support
Support
- Email and self-service support for Free and Standard plans
- 24/7 premium support with response time SLAs (Premium/Enterprise only)
- Community, help center, and on-demand training
Pros
Cons
Why we picked Jira
Jira is purpose-built for Agile software development teams. From backlogs and sprint planning to bug tracking and release management, Jira gives devs and technical teams everything they need to plan, execute, and iterate. If you’re running agile sprints, writing code, or managing releases, Jira is your best bet.
Jira’s key difference: Integration with software development tools
Jira carves out its own space in the project management tool category with its robust integration with software development workflows, particularly agile methodologies. Designed specifically for software development teams, Jira offers powerful features for managing tasks, sprints, and releases using frameworks like Scrum and Kanban. This tailored approach empowers teams to plan, track, and deliver software projects more consistently, boosting collaboration and visibility throughout the process.
READ MORE: monday.com vs Jira Comparison: Which is the Best Project Management Tool?

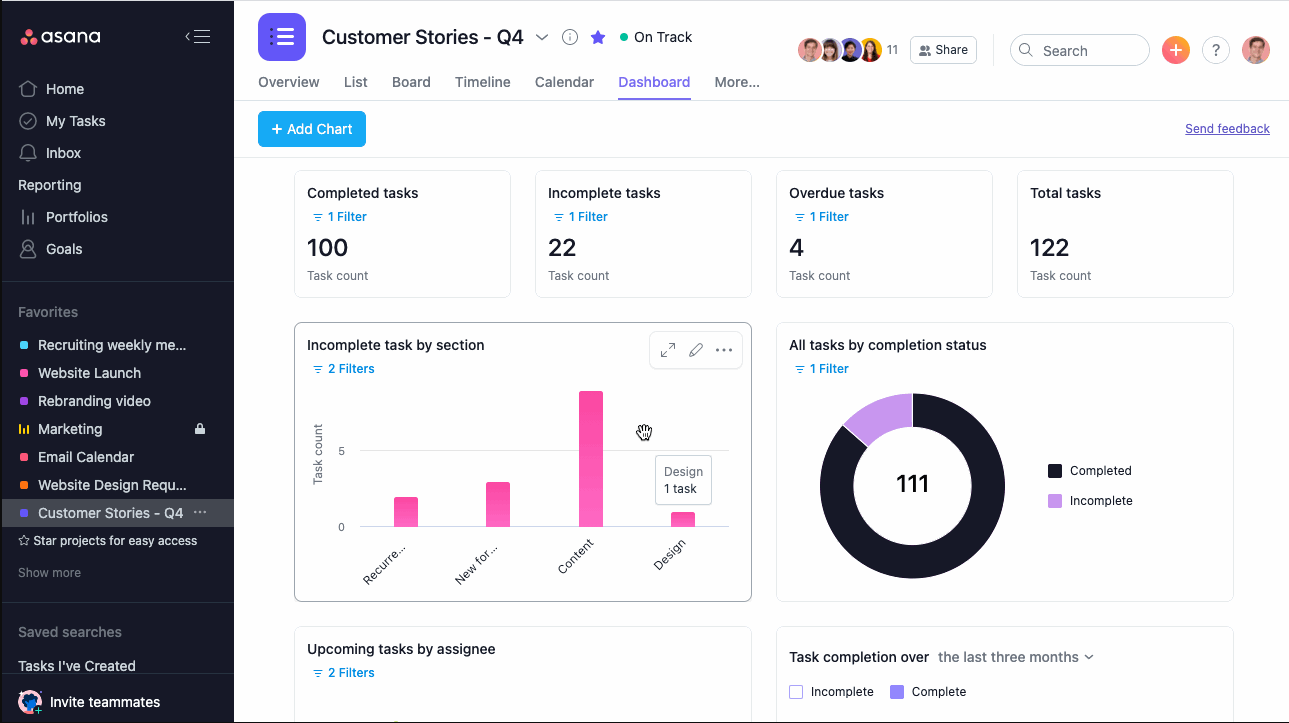
Asana — Best for remote teams
Asana is a comprehensive project and task management tool that offers a user-friendly interface for teams to organize and track work. This cloud-based task management solution provides multiple view options, such as lists, timelines, and boards, to visualize project data and progress.
With a free plan available for up to 15 users, Asana supports task assignments, workflow customization, bug tracking, sprint management, and planning for campaigns and product launches. It also includes features like messaging, file storage, unlimited dashboards, automation, and mobile apps.
Asana’s mobile app comes with features trailor-made for mobile devices. Some of these functions include automatically filling in tasks by transcribing the user’s voice or taking a photo ans turning it into text; archiving, bookmarking, and creating follow-up tasks with just a single tap; and commenting, uploading attachments, and tagging teammates in important updates.
While Asana offers a rich feature set, the inability to assign tasks to multiple users at once can be a limitation in complex workflows, though tagging additional users provides a workaround.
Screenshots
Standout features
- Timeline view for visualizing project schedules and dependencies
- Rules automation builder to streamline repetitive tasks
- Portfolios and Workload views to manage team bandwidth
- Built-in messaging, file sharing, task comments, and @mentions
- AI work assistant that suggests deadlines, flags blockers, and summarizes updates
Key integrations
- Slack, Zoom, Microsoft Teams — real-time collaboration
- Google Workspace, Outlook — calendar, task sync, email to task
- Salesforce, HubSpot — CRM integrations
- Jira, GitHub — for hybrid tech teams
- Zapier, Make, Tray.io — no-code automation
These integrations help remote teams work across tools without friction, maintaining visibility and momentum.
Pricing
- Basic (Free): Up to 15 users, unlimited tasks/projects
- Premium: $10.99/user/month — timelines, rules, custom fields
- Business: $24.99/user/month — portfolios, workload, integrations
- Enterprise: Custom pricing — advanced controls, SSO, 99.9% uptime SLA
Support
- Email and help center included in the Free and Premium plans
- 24/7 chat and dedicated success managers on Business and Enterprise
- On-demand webinars, certification courses, and an active community
Pros
Cons
Why we picked Asana
Asana makes remote work easier. With strong visual tools, seamless communication features, and advanced automation, it’s perfect for distributed teams that need to stay aligned, no matter where they are. Its clarity, flexibility, and integrations help global teams move work forward, making Asana one of the best tools for remote collaboration.
Asana’s key difference: Intuitive interface
What makes Asana unique is its interface that is designed with a focus on visual task management and team collaboration.
Asana’s interface includes intuitive drag-and-drop functionality, customizable project views, and visually appealing task boards. This focus on visual task management increases team productivity and engagement by providing a clear and obvious way to organize tasks, track progress, and communicate priorities. The visual nature of Asana makes it easier for teams to determine project status at a glance, identify bottlenecks, and collaborate for better project outcomes.
Read our complete Asana software review.

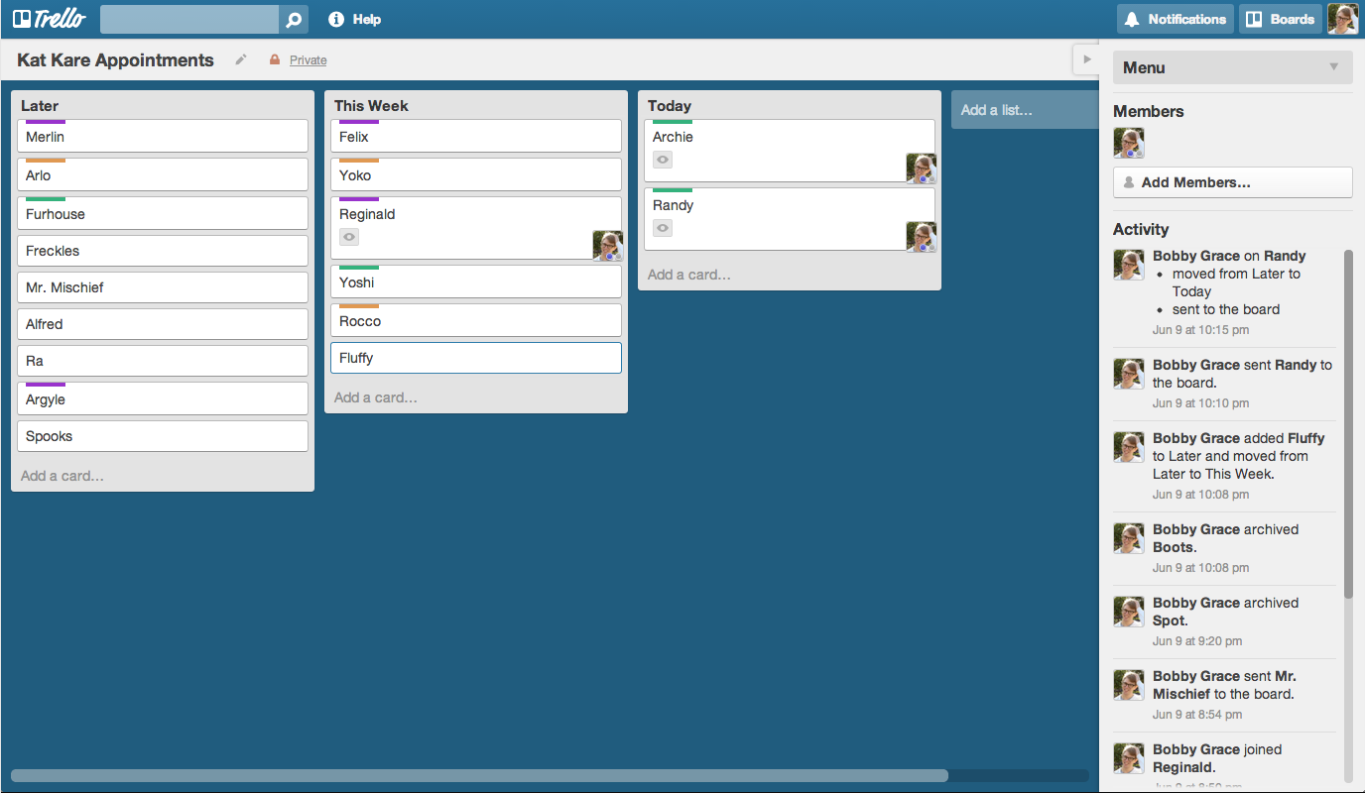
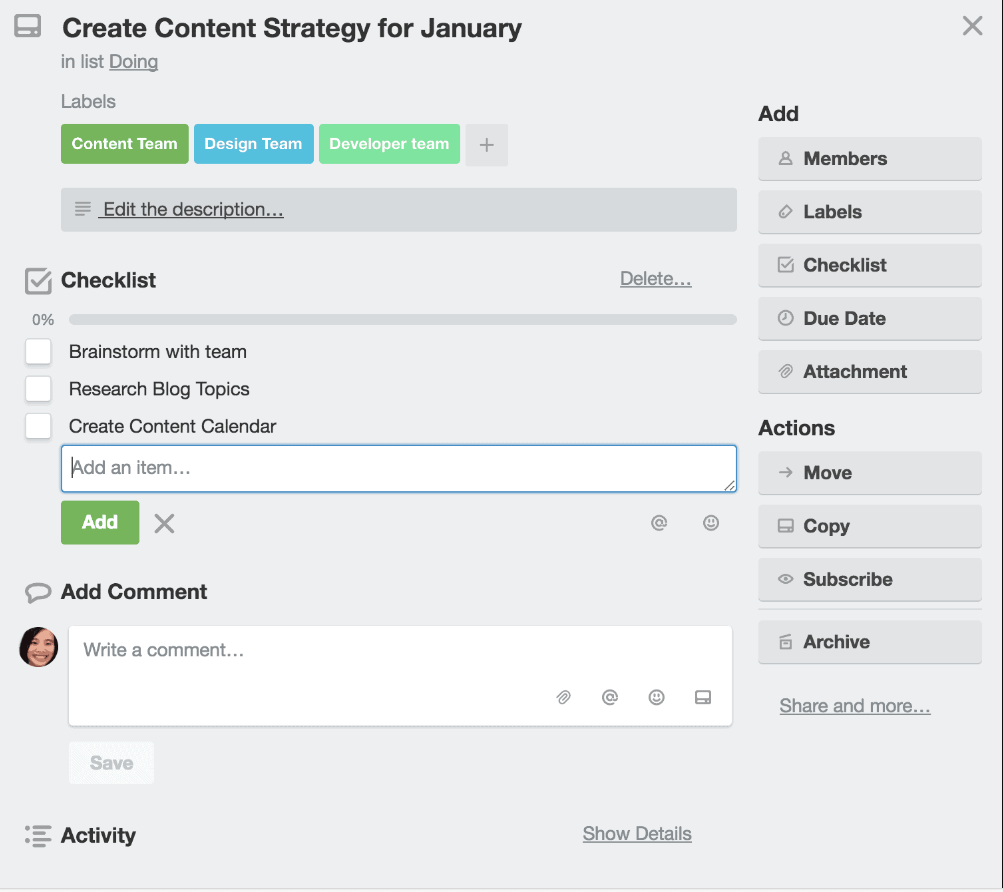
Trello — Best for smaller projects and teams
Trello is a highly visual, web-based project management tool that uses a kanban-style board to organize tasks into cards and boards. This layout makes it easy for project managers to see what’s being worked on, who’s responsible, and the status of tasks and subtasks.
Trello’s simple, intuitive design allows users to quickly add, move, and prioritize tasks, making it ideal for teams who need to transform a list of tasks into an actionable plan. Its flexible setup is perfect for organizing projects in phases and keeping track of deadlines efficiently.
Trello also has a mobile app that is built with features that help you stay updated and connected with your team while on the go, such as adding teammates to your workspace, replying and reacting to updates from a push notification, and scanning images for text using an iOS device.
Screenshots
Standout features
- Kanban boards with cards, checklists, due dates, attachments, and labels
- Workspace views: Calendar, Table, Dashboard, and Timeline
- Butler automation engine for setting rules, triggers, and custom buttons
- AI-powered card summaries and task suggestions
- Board templates for marketing plans, product launches, sprints, and more
Key integrations
- Slack, Microsoft Teams, and Zoom for easy updates and collaboration
- Google Drive, Dropbox, and OneDrive for file storage
- Salesforce and HubSpot for CRM tracking via Power-Ups
- GitHub and Bitbucket for for dev teams
- Zapier and IFTTT to connect nearly any other tool
Trello’s Power-Up system makes it adaptable without adding complexity, perfect for lightweight use cases.
Pricing
- Free: Unlimited cards, up to 10 boards per Workspace
- Standard: $5/user/month — unlimited boards, advanced checklists
- Premium: $10/user/month — timeline, dashboard, calendar views
- Enterprise: Starting at $17.50/user/month — user management, security,support
Support
- Help docs and community for free users
- Email and priority support on paid plans
- Admin support and onboarding on Premium and Enterprise plans
Pros
Cons
Why we picked Trello
Trello is beloved for its simplicity. It uses Kanban boards and drag-and-drop cards to help teams quickly organize projects, visualize workflows, and get started with zero friction. It’s ideal for individuals, startups, or small teams who value speed and clarity over complexity.
Trello is the perfect starting point for visual project management. If you want to organize work without a steep learning curve — or just love sticky notes — Trello delivers a streamlined experience for simple task planning.
Trello’s key difference: Kanban boards
Trello’s strength lies in its simplification and representation of tasks and their priority. Users organize tasks on Kanban boards using cards. These customizable boards represent different projects, with lists indicating workflow stages and cards representing individual tasks. Trello’s visual organization simplifies project management so teams can easily understand project status, track progress, and collaborate to get work done.
READ MORE: Notion vs Trello: Which Tool Is Best for Your Business?

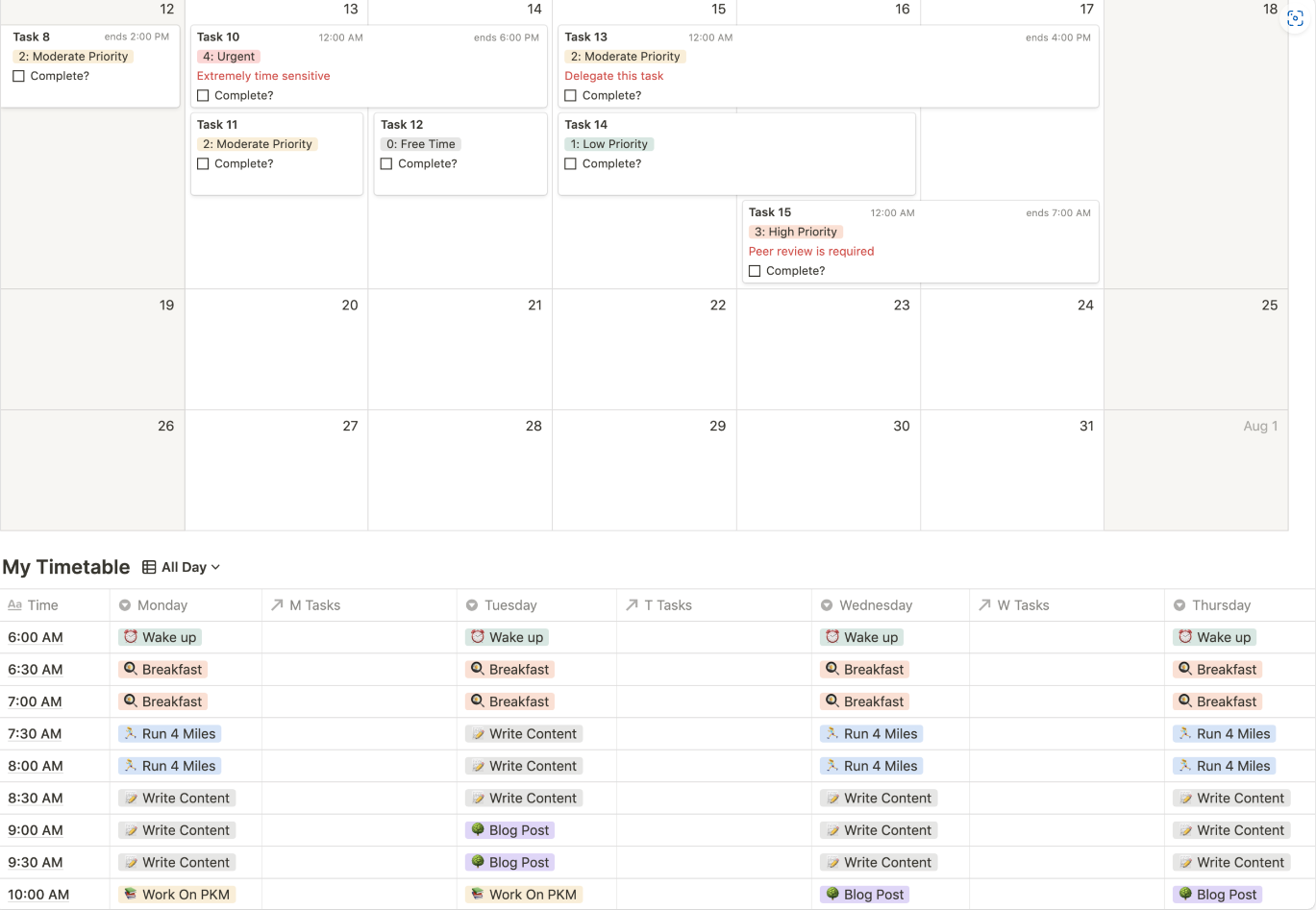
Notion — Best for creative teams
Notion is a highly adaptable, all-in-one project management platform that offers tools for project management, task tracking, team wikis, vision boards, and more. Its customizable features make it suitable for a wide range of team needs, from creative brainstorming to execution and tracking.
Notion’s visually appealing design and user-friendly interface have gained the tool popularity among creatives who need to collaborate and organize their work in a single, centralized space.
Standout features
- AI tools for drafting copy, summarizing content, and automating updates
- Drag-and-drop blocks for creating custom project pages, task boards, or wikis
- Timeline, calendar, kanban, and database views
- Meeting scheduler and enhanced calendar sync
- Full-page comments, collaborative editing, and in-line media embedding
- An app that is optimized for mobile, allowing users to read, edit, and comment while on the go
Key integrations
- Slack, Zoom, and Microsoft Teams for in-app messaging and meetings
- Google Calendar, Notion Calendar (beta), and Outlook for schedule syncing
- Figma, Miro, and Loom for embedding creative assets
- GitHub and Jira for dev teams
- Zapier and Make for automating external workflows
These integrations make Notion ideal for design, marketing, product, and hybrid creative-tech teams.
Pricing
- Free: For individuals and up to 10 guests, basic blocks and collaboration
- Plus: $8/user/month — unlimited file uploads, sharing, version history
- Business: $15/user/month — private teamspaces, advanced permissions
- Enterprise: Custom — SAML SSO, audit logs, compliance tools
Support
- Help center, video tutorials, and a vibrant user community
- Priority support for Plus and Business plans
- Dedicated account manager for Enterprise users
Pros
Cons
Why we picked Notion
Notion is more than just a project management tool — it’s a highly customizable all-in-one workspace. Its flexibility lets creative teams organize tasks, docs, wikis, design ideas, and meeting notes — all in one spot. Think of it as your digital creative studio.
Notion is a cloud-based platform that is tailor-made for creatives and multidisciplinary teams who want one tool for everything — tasks, ideas, notes, content, and planning. If your team likes thinking outside the box, Notion gives you the sandbox to do it all.
Notion’s key difference: All-in-one workspace
Notion takes the trophy as an outstanding all-in-one workspace for managing work. From note-taking and document collaboration to knowledge management and database management, Notion can handle it. Its versatility streamlines workflows, eliminating the need to juggle multiple tools. Teams can tailor their workspace to their specific task and collaborate with ease no matter the industry or team size.
Learn more in our Notion software review.

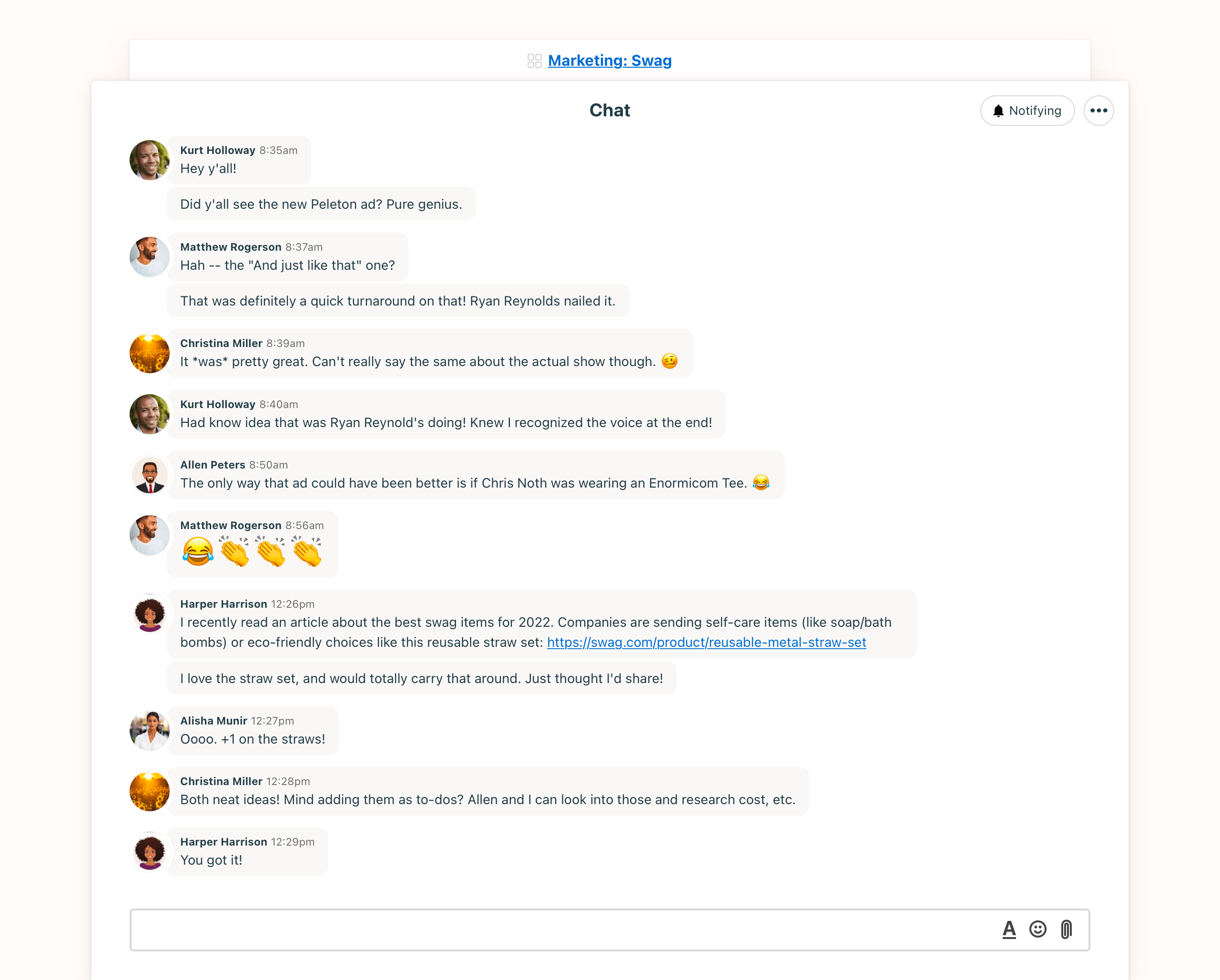
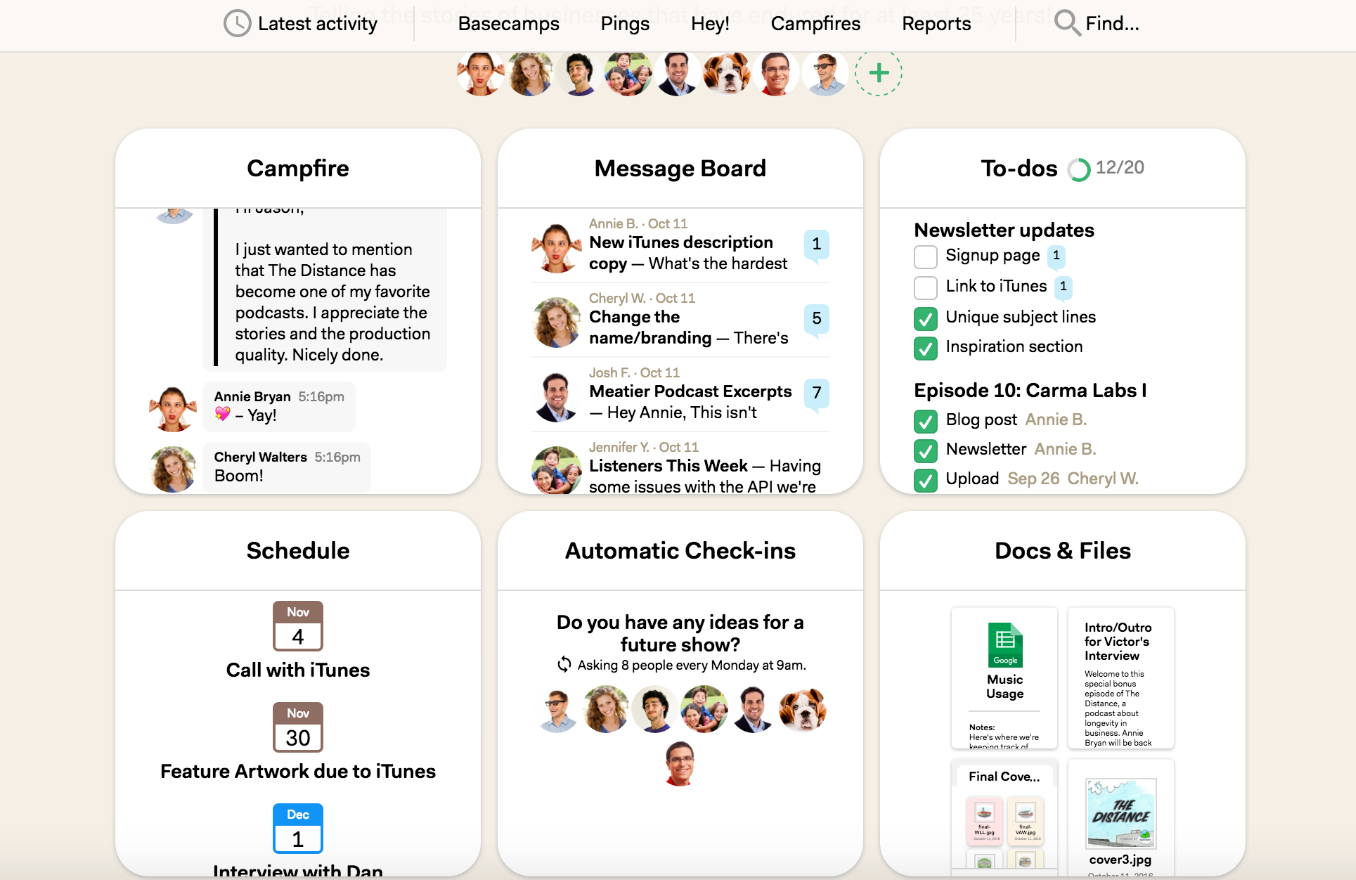
Basecamp — Best for collaboration
Basecamp is a versatile web-based project management tool that integrates team communication features, making it ideal for remote work environments. It helps teams stay organized by offering tools for task management, file sharing, project planning, and real-time updates. With a simple, unified interface, Basecamp enables collaboration through message boards, group chats, and direct messaging.
Basecamp has a mobile app where you can see all of your projects and stay caught up with changes and progress even when you’re not at your desk. The app has a Kanban-style Card Table view that allows you to track tasks easily.
Basecamp, however, does not have a free plan but offers a 30-day free trial. After the trial, you can switch to their lower-tier plan, which costs $15 per user per month. The plan includes access to all features for unlimited users and projects, including to-do lists, scheduling, file sharing, charts, and automated reports.
Standout features
- To-do lists, task assignments, and due dates across multiple projects
- Message boards, direct messages, and Campfire real-time chat
- Centralized file sharing with version control and client access
- Automatic check-ins: prompt your team for updates without a meeting
- Kanban board–based Card Table view for simple workflows
Key integrations
- Slack, Zoom and Microsoft Teams for real-time chat and meetings
- Google Workspace, OneDrive, and Dropbox for document and calendar syncing
- Zapier to connect the tool with CRMs, time trackers, invoicing tools, and more
These integrations make Basecamp a strong choice for collaborative work and for creative agencies, consultancies, and client-facing teams who want everything in one spot.
Pricing
- 30-day free trial
- Basecamp Plus: $15/user/month — includes all features
- Basecamp Pro Unlimited: $299/month flat rate — unlimited users and storage, ideal for larger teams
Support
- Email support (Monday–Friday), 24–48 hours response window
- Rich help library, tutorials, and onboarding videos
- Priority support available for Pro Unlimited users
Pros
Cons
Why we picked Basecamp
We picked Basecamp because of how it puts frequently accessed tools and information in one place. It reduces meetings and eradicates scattered chats by providing a calm, centralized space that is easily accessible to all team members — an especially useful feature for remote or hybrid teams.
Basecamp shines where clear communication is more important than complex planning. It’s ideal for collaborative teams who want a single workspace for tasks, files, conversations, and updates, especially when working with clients or external vendors.
Basecamp’s key differences: Simplicity and ease of use
Basecamp is a popular choice among project teams because of its focus on simplicity and user-friendliness. It offers a streamlined interface and straightforward features that minimize complexity, providing a smooth learning curve for users. Teams can quickly onboard and instantly utilize the software to manage their work without having to navigate intricate features. Its built-in tools foster real-time communication across teams.
Read our complete Basecamp software review.

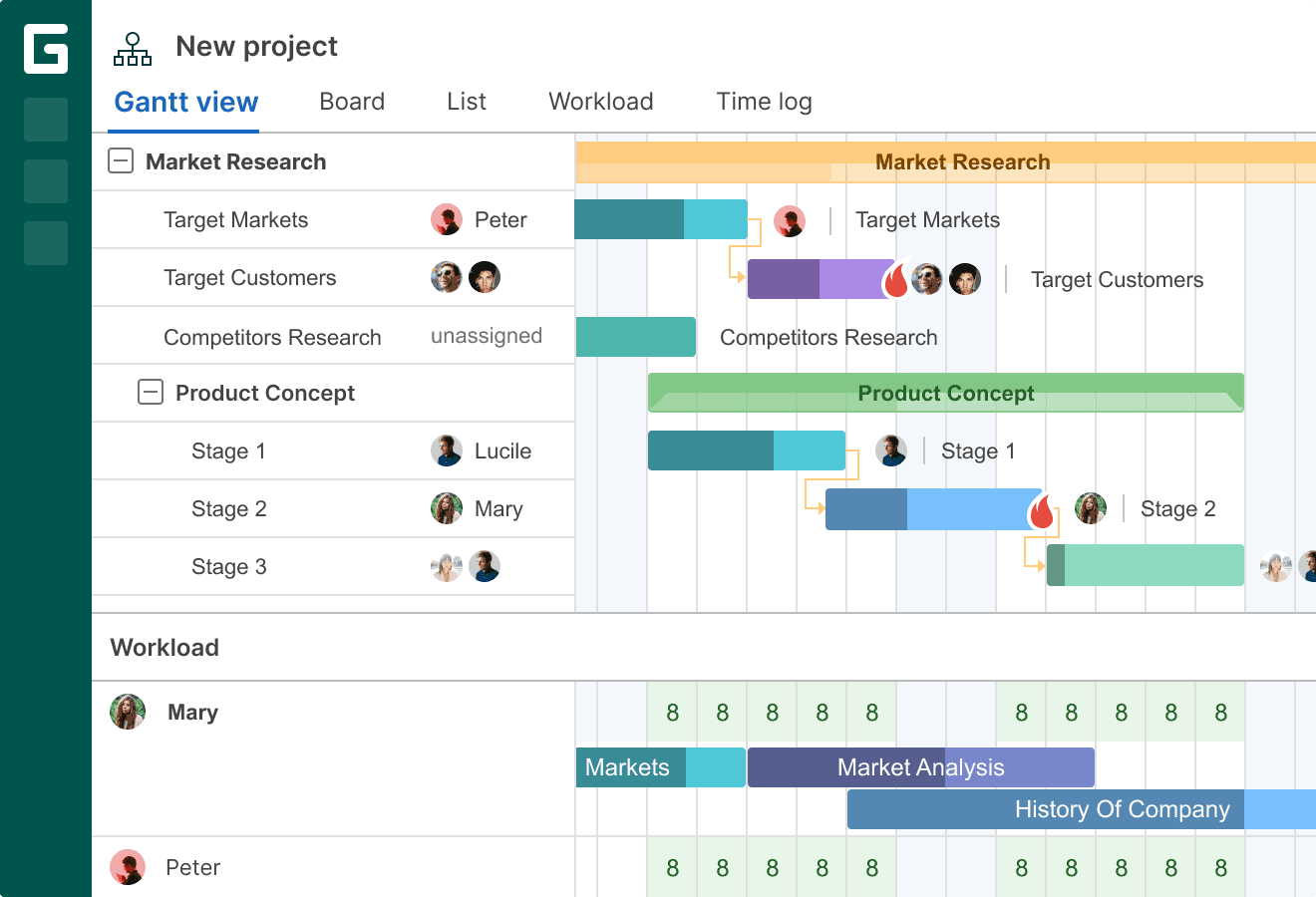
GanttPRO — Best option for beginners
GanttPRO is an excellent project management tool for beginners, offering an intuitive, user-friendly interface and a robust free plan. It’s ideal for users new to project management software, providing essential tools to manage tasks and timelines effectively.
As teams grow and their needs become more complex, GanttPRO scales to support more advanced project management features, making it a versatile solution that evolves with the user’s requirements.
As GanttPRO is a cloud-based software, users can use it to manage their projects using any type of device and with any operating system. GanttPRO’s mobile app is available for download for users on any plan and offers core functionalities like creating tasks, responding to comments, and tracking time.
Screenshots
Standout features
- Elegant drag-and-drop Gantt chart interface with dependencies and baselines
- Task assignments, progress tracking, priority settings, and milestones
- Ready-made templates for IT, construction, marketing, and product management
- AI-powered suggestions for task duration, team assignment, and timeline optimization
- Export projects to PDF, PNG, Excel, or XML formats for presentations and reports
Key integrations
- Slack, Zoom for communication and task notifications
- Google Drive, OneDrive, and Dropbox for file attachments and syncing
- Jira and Trello to sync tasks for hybrid workflows
- API access and Zapier integration to connect with 3,000+ other tools
These integrations make GanttPRO capable of growing with your team, especially in industries like construction, event planning, education, and client services.
Pricing
- 14-day free trial
- Basic: $7.99/user/month — includes core features, Gantt view, and collaboration
- Pro: $12.99/user/month — adds advanced scheduling, time tracking, and more integrations
- Business: $19.99/user/month — adds portfolios, workloads, and custom fields
- Enterprise: Custom — adds SSO, audit logs, and dedicated onboarding
Support
- Monday–Friday email and chat support on all paid plans
- Tutorials, documentation, and live onboarding sessions
- Priority onboarding and training on the Enterprise plan
Pros
Cons
Why we picked GanttPRO
We chose GanttPRO because it makes project planning visual and straightforward, especially for beginners who want a clear overview of timelines, dependencies, and team assignments. With an intuitive Gantt chart interface and easy onboarding, it’s great for users who don’t want to feel overwhelmed by complex tools. GanttPRO also helps users get organized fast without sacrificing clarity or structure.
GanttPRO’s key differences: Sophisticated Gantt chart and intuitive interface
GanttPRO sets itself apart from almost every other project management tool that includes a Gantt chart by offering a sophisticated Gantt chart view set within an intuitive interface. It strikes a fine balance between project planning and tracking through drag-and-drop functionality, which any user can learn and use to their advantage when organizing and prioritizing tasks.
Read our complete GanttPRO software review.
What is project management software?
Project management software is a digital tool used to plan, schedule, track, collaborate, and report on projects of any size. These platforms help project managers and their teams stay organized, communicate effectively, and deliver work on time and within budget. Whether it’s assigning tasks, managing resources, or visualizing timelines, project management software centralizes everything into one place.
For example, a marketing team at a mid-sized company might use Asana to coordinate a product launch. Each team member receives tasks with deadlines, while managers can view progress through Kanban boards and Gantt charts. Files, feedback, and updates stay within the task itself, reducing email clutter and time spent on waiting on approval.
Meanwhile, a software development team could rely on Jira to track bugs, manage sprints, and collaborate using agile methodologies. Developers log issues, update statuses, and collaborate with designers and QA engineers all within the same workspace. Jira’s integration with GitHub and Confluence streamlines code management and documentation.
Even small businesses or freelancers can benefit from tools like Trello or ClickUp. A freelance designer, for instance, might use Trello to manage client projects with boards for “To-Do,” “In Progress,” and “Completed.” This setup keeps clients informed and makes revisions easier to track.
Project management software helps teams assign and monitor tasks, track time, budget, and scope, collaborate in real time, minimize delays and errors, and keep stakeholders aligned. From enterprise giants to remote startups, PM software is a must-have tool for driving productivity, accountability, and success in any project-driven environment.
What are the different types of project management software?
There are many types of project management solutions to consider. Desktop project management applications offer advanced features, scalability, and security to support multiple users and groups over an internal network. Cloud-based project management tools have made it possible for vendors to offer sophisticated, subscription-based solutions to businesses of all sizes, making it so users can access the tool from any location.
When selecting project management software for your business, these are the main types and formats you’ll need to consider:
What are the most important features of project management software?
Choosing the right features for your team will depend on the size of your team, the complexity of the projects you run, and the project types and use cases you work with. Prospective PM software buyers should look for the following features:
What to Consider When Purchasing Project Management Software?
| Business type | Key considerations | Industry-specific use cases (with tool examples) |
| Small business | • Simple, affordable solutions • User seats • Easy visualizations | •. Creative freelancers can use ClickUp for flexible task tracking. • Startups or marketing teams benefit from Trello’s Kanban-style simplicity. • Small construction or retail shops can get started quickly with GanttPRO. • Agencies that prioritize team communication may prefer Basecamp. |
| Midsize business | • Better integrations and time-tracking features • Scalable reporting and dashboards | • Fast-growing teams in retail or manufacturing may choose Smartsheet for automation and form-based workflows. • Remote teams like NGOs or tech firms can thrive using Asana for transparent task assignment. • Creative teams can centralize docs and projects with Notion. |
| Enterprise | • Security, admin controls, and scalability • Deep integrations with ERP and BI tools | • Enterprise IT, HR, or operations teams benefit from monday work management for customizable workflows and team dashboards. • Engineering or legal teams prefer Wrike for tailored permissions and detailed workflows. • Software development teams at scale use Jira for Agile and Scrum methodologies |
Recent trends in project management
AI tools in project management software
AI now plays a crucial role in enhancing efficiency and decision-making and is used to predict outcomes, allocate resources, and make recommendations by quickly analyzing all project parameters and team member details.
Focus on automation
Automating routine tasks such as scheduling, reporting, and risk management is a game-changer, significantly reducing manual effort and time spent on repetitive work. Advanced automation features in modern project management tools now go beyond simple task reminders — they dynamically update project timelines, auto-generate reports, assign work based on capacity, and even detect at-risk tasks before they become delays.
For example, in monday work management, a marketing agency can set up automation rules to reassign overdue tasks, notify stakeholders when a milestone is reached, or trigger budget updates when a task is marked complete. This reduces the need for constant check-ins and manual updates, helping teams stay productive and aligned, especially when managing multiple campaigns at once. As a result, teams spend more time doing the work and less time managing it.
Hybrid project management methodologies
A combination of elements of both agile and traditional waterfall approaches, this now-common hybrid methodology is prevalent across teams. It requires a project manager or lead to build both ways into a master timeline to accommodate all teams and the work they perform.
Data-driven decision-making
Enhanced data analytics help project managers improve forecasting, optimize workflows, and make smart decisions when it comes to scheduling, budgets, and allocating resources. Data drives accuracy and smart decisions whether you are planning, forecasting, allocating, or optimizing.
Flexible work environments
This involves predominantly remote teams with adaptable work hours, locations, and schedules. Project managers must embrace a fluid approach to accommodate these flexibilities, including seamless onboarding for team members stepping in during leave of absence, sick time, or planned time off. The key lies in agile scheduling and task management to make sure operations run smoothly despite varying circumstances.
Use of all-in-one platforms
All-in-one platforms can handle everything from initial planning to reporting. By integrating with other software and tools, they allow you to create a customized process and system for all of your projects. These platforms are collaborative and give you insight into real-time updates and 24/7 access to critical data.
PMOs
Project management offices (PMOs) have evolved significantly. Once purely administrative, they now play a strategic role. PMOs align with business goals, manage portfolios of work, and drive organizational change. Virtual PMOs and centralized oversight committees give much-needed support to diverse teams.
Tips for rolling out project management software for your business
Companies should carefully plan how they roll out new project management software. The responsible project manager will need to first get the support of major stakeholders, from C-level executives to end users on the project team. From there, project managers should create a schedule that allocates time for learning how to use the software before taking on a major project. That way, each and every project will be set up properly.
Finally, be ready with onboarding and training materials, as well as support documentation, to ensure individuals don’t have to spend too much time learning about these project management programs and can quickly pivot back to their normal workloads.