Malicious cyber campaigns that threaten private companies, government agencies, and the general public continue to increase in frequency and sophistication. Endpoint detection and response (EDR) tools can work together with other security solutions to provide real-time protection.
Read also: Project Management Techniques Used by Hackers
Table of Contents
What Are EDR Tools?
Endpoint detection and response tools provide real-time monitoring to detect malicious activity. In the past, security professionals put in place systems like endpoint protection platforms (EPP) to block attacks before they happened. Prevention is still an important part of effective defense. However, perfect prevention is not yet achievable, so combining prevention with detection results in a more successful approach.
EDR security tools work as another level of protection, should an attack manage to get past a firewalll. These systems also promote visibility through continuous monitoring and recording of activities that take place at endpoints.
Today’s EDR systems use advanced analytics that can detect unusual patterns of behavior and alert IT administrators to a possible breach. These solutions also complement antivirus systems by detecting suspicious activities not yet recognized or identified by antivirus software.
Back to top
Best EDR Tools
EDR security provides users broad visibility by collecting comprehensive data, which serves as the foundation of detection and response. The best EDR software includes advanced analytic techniques to interpret collected data, as well as simplifing investigations so IT personnel can respond quickly.
Here is our list of top EDR software to provide businesses and organizations of all sizes real-time endpoint security.
Cisco Secure Endpoint

Cisco Secure Endpoint is a cloud-native solution that users can deploy through a public or private cloud. It integrates prevention, detection, threat hunting, and response features to protect Windows, Mac, Linux, iOS, and Android devices. Its comprehensive protection capabilities help users prevent breaches and block malware at the point of entry. It also continuously monitors and analyzes file and process activity to detect, contain, and remediate threats.
Cisco Secure Endpoint has powerful EDR capabilities that reduce the attack surface. Advanced search helps simplify investigations at endpoints, so users get the answers they need fast. The built-in SecureX platform gives users a unified view, while threat hunting teams help identify threats found within the customer environment.
Pros
- Accurate identification of infected endpoints and new threats
- Low false-positive rate
- Automated remediation without user intervention
Cons
- Needs an easier way to integrate with non-Cisco products
- Customers wish for more direct access to AMP support agents
Palo Alto Networks Cortex XDR

Palo Alto Networks offers Cortex XDR, a security solution that integrates network, endpoint, and cloud data to stop sophisticated, malicious attacks. Extended detection and response (XDR) tools are an upgrade of EDR solutions, with additional features and capabilities that include blocking malware, exploits, and fileless attacks using behavioral threat protection, AI, and cloud-based analytics.
Cortex XDR uses behavioral analytics and machine learning to profile behavior and detect anomalies that attempt to blend in with legitimate activity. It provides a complete picture of each attack and gives alerts, artifacts, MITRE tactics so users can stop attacks swiftly. This complete endpoint security solution includes next-generation antivirus (NGAV), host firewall, disk encryption, USB device control, deep forensics, and flexible response.
Pros
- Advanced behavioral analytics with detailed information and alerts
- Extended monitoring and tracking of endpoints, networks, and cloud data
- Comprehensive investigation and querying tools
Cons
- Information on screen can sometimes be overwhelming
- Complicated implementation for Mac
McAfee MVISION EDR

McAfee MVISION EDR simplifies endpoint detection and response with its AI-guided threat investigation. With built-in threat intelligence, it enables security analysts of all levels of experience to detect and respond to priority threats without spending time chasing too many leads. The software continuously gathers, summarizes, and visualizes evidence from multiple sources, minimizing the need for additional security operation center (SOC) resources.
McAfee MVISION automatically identifies key findings, so users do not have to spend too much time on manual evaluation. Users can deploy the solution on premises or as a SaaS solution. Several related products enhance Microsoft Windows basic security controls, centralize management of Microsoft Defender, and provide on-device protection of iOS and Android devices.
Pros
- Good visualization tools for enhanced visibility
- Easy to use, and a good balance of cost to value
- Asset inventory features
Cons
- Can slow down workstations because of heavy processes
- May affect the performance of browsers during search
Cybereason Defense Platform

Cybereason Defense Platform provides scalable endpoint security, with different plans for all business sizes. It offers a solution for small businesses focused on prevention, for midsize companies defending against cyber threats, or for enterprises in need of more advanced SOC tools. This endpoint security tool provides a unified approach that enables users to quickly correlate threat activity across the network, protecting both fixed and mobile endpoints.
Cybereason EDR features include threat intelligence that aggregates and cross-examines multiple threat feeds to determine the correct source, enabling users to respond quickly. It also has instant remediation that ranges from machine isolation, to process killing, to persistent mechanism removal. Other features include high speed, an accurate correlation engine, ML-powered detection, and research-driven insights.
Pros
- Comprehensive detection tools with high accuracy
- User-friendly interface
- Easy to deploy
Cons
- Needs additional reporting features, especially for management
- Users wish for more responsive customer service
CrowdStrike Falcon Insight

Falcon Insight from CrowdStrike provides users continuous and comprehensive visibility through detection, response, and forensics. Continuous monitoring captures endpoint activity to give users visibility on endpoint threats. It also delivers deep analysis that automatically detects suspicious activity indicating stealthy attacks and breaches.
Falcon Insight helps improve security operations efficiency, allowing analysts to spend less time on handling alerts. The company also offers additional Falcon and standalone modules, specialized products, as well as an app store.
Pros
- Positive feedback from many customers expressing high confidence in the product
- Allows custom block and exception rules
- Extensive API for easy integration
Con
- Needs improvement in vulnerability management
- Additional cost for new features
SentinelOne Singularity XDR

Singularity XDR from SentinelOne unifies separate functions into a single agent and platform architecture. It provides end-to-end visibility, powerful analytics, and automated response. Its aim is to stop sophisticated attacks against endpoints, as well as IoT, cloud workloads, and edge points without analyst intervention.
Singularity XDR finds threats with autonomous, real-time, and index-free threat intelligence and analysis that supports structured, unstructured, and semi-structured data. It automatically correlates disparate data to uncover malicious behaviors and techniques. Other EDR solutions included in the software are automation of response and remediation, built-in integrations, and a consolidated view of alerts across security layers.
Pros
- Real-time threat protection that includes zero-day threats
- Reliable automated response
- Lightweight agent that works offline
Cons
- Missing disk encryption
- Needs easier client onboarding and a more accessible knowledge base
BlackBerry Optics

BlackBerry Optics is a cloud-native solution that provides on-device detection and remediation across the organization. Context-driven threat detection rules powered by Cylance AI can identify
security threats and trigger automated responses in reduced time. This solution provides an enterprise-wide view of all endpoint activities to detect and respond to both online and offline devices.
BlackBerry Optics includes an intuitive query language to allow analysts to hunt threats and discover root causes. It also has the option to retain 365 days of data for deep investigation. Other features include automated forensic events logging, custom detection rules, integrated MITRE ATT&CK, private network visibility, and advance scripting visibility.
Pros
- Intuitive, easy to navigate, and highly automated
- Easy reporting for executives
- Effective against ransomware and unknown threats
Cons
- Needs additional documentation
- Server implementation can be challenging
Comodo Dragon EDR

Comodo Dragon EDR provides endpoint protection with advanced threat hunting and expanded endpoint visibility. Users get continuous real-time visibility with endpoint threat detection, allowing security teams to identify attacks with accurate root cause analysis. The software gives actionable intelligence, prioritizes security incident reporting, and issues alerts using a lightweight agent on endpoint devices, with updates delivered via the cloud.
Dragon EDR provides forecast analysis, timeline response, and threat visualizations. Users get an early warning, as well as detection and post-detection visualization. It tracks malicious processes on endpoints and can send real-time email and SMS alerts to reduce notification time.
Pros
- Easy-to-use interface
- Good visibility of resources and tools
- Whitelisting capability
Cons
- Installation could be simpler
- Noted instances of system lock that require physical, on-site user intervention
Cynet 360

Cynet 360 is an EDR security solution for the enterprise. It provides endpoint protection and automated investigation and remediation actions — with 24/7 support from a managed detection and response (MDR) service at no additional cost. The solution uses advanced detection techniques to detect potential threats, provides full visibility, and also deploys deception technology to detect stealthy attacks.
Cynet 360 uses combined telemetry to provide visibility and protection across the entire attack surface. It natively combines and coordinates key security controls like NGAV, EDR, network traffic analysis (NTA), user behavioral analytics (UBA), and deception using various types of decoy files. It also automates investigations and incident response with pre-built and custom remediation, as well as using remediation playbooks for various attack scenarios.
Pros
- Easy installation and deployment
- Highly automated response and remediation
- Free managed services included
Cons
- Needs better coverage on Android endpoints
- Needs improvement in dashboard and reporting features
CrowdSec

CrowdSec is a free, open-source, and multi-player security solution for Linux. It is a collaborative EDR that leverages crowd power, allowing users to analyze behaviors, respond to attacks, and share signals across the community. The software can run on virtual machines, bare-metal servers, or
containers.
Users can call CrowdSec from code through its API. CrowdSec shares the IP addresses of attackers across the community and enables the platform to curate and redistribute a qualified IP blacklist to all users. It decouples detection (agent) and remediation (bouncer), so it does not create a single point of failure and can fit different topologies. Written in Golang, it can parse massive amounts of logs quickly. Other features include dashboards, support for IPv4 and IPv6, and GDPR compliance.
Pros
- Free and open source
- Customizable
- Crowdsourced and curated IP blacklisting
Cons
- Only supports Linux and FreeBSD platforms
- Needs additional bouncers or remediation tools
Back to top
Types of EDR Tools
More organizations are exploring endpoint detection and response solutions because of the rising occurance of breaches. Further, more affordable EDR software is now offered by many vendors. Companies can choose the right solution for their needs by understanding the different types available.
Agent-based
Some EDR software uses agents, or small software components that the EDR installs in every endpoint device. The agent collects data on user activity and transmits the data to a central server for processing, analysis, and storage. Agents can capture extensive details and processes on the endpoint device.
Agent-based EDR can capture user activity and record it to a local cache for later transmission. Agents allow interactive intervention in a user’s device, such as quarantining, if needed.
Agent-less
Agent-less EDR are quicker to deploy, as there’s no need to install agents on every device. It can monitor endpoints that are especially difficult to install agents on, or those that cannot accept agent components. The solution also does not consume resources on the endpoints, nor require overhead or personnel to install and manage agents on endpoints.

Hybrid
Some EDR platforms use both agent-based and agent-less systems for a greater coverage of endpoints. These systems offer better data collection on devices that can have agents, and quick deployment to monitor endpoints that cannot accept agents. Hybrid solutions use both technologies to overcome the shortcomings of either solution.
Standalone
In the past, EDR products were standalone threat-hunting software installed to monitor endpoints. Some vendors still offer this type of solution, especially to managed service providers (MSPs). In this way, providers can offer alternative EDR services to a customer, even when a solution from a different vendor is in place.
Integrated
Most of today’s EDR software integrates into EPPs to combine both prevention and detection, resulting in several layers of security. Integrated solutions also support more types of operating systems, devices, and connections. These tools can provide EDR security to individual user computers, mobile devices, and IoT devices connecting remotely, as well as those within the corporate network.
XDR
More EDR vendors are transitioning their products from EDR to extended detection and response. XDR tools provide security not only to endpoints, but also to different types of network and cloud workloads. XDR allows vendors to offer a single platform that covers all the customer’s computing devices, whether on-premise, on remote networks, or as virtual machines connected to cloud platforms.
Deployment
Some EDR platforms are available through proprietary hardware or security appliances. This box contains the software, hardware, and connection ports. Other tools are available as downloaded and installed software on customer-owned computers, while others are available via the cloud. Although most solutions are now delivered from the cloud, this does not automatically mean the solution can cover the security of cloud components and endpoints.
Back to top
Common Features of EDR Tools
EDR software provides many benefits that complement other cybersecurity measures. With EDR, users can prevent data breaches, detect stealthy threats, gain real-time visibility across all endpoints, and accelerate incident response. To enable comprehensive endpoint detection and response, EDR platforms need to have the following essential features.
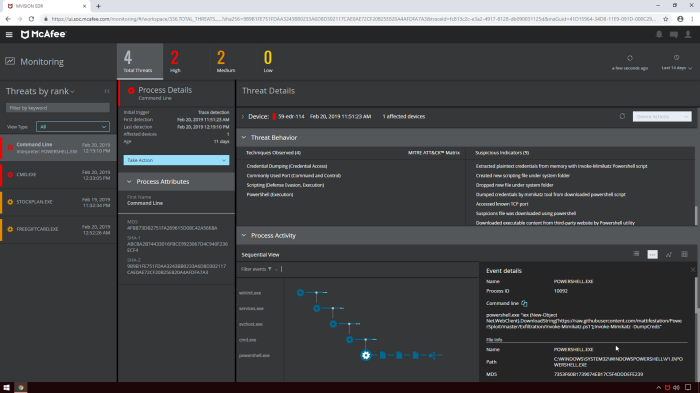
Continuous Monitoring
EDR software continuously monitors, or at least monitors at regular intervals, all endpoint activity. By monitoring, the tool can keep watch of processes and runtimes to identify abnormal behavior using advanced behavioral analysis and algorithms. The software compares activities with the latest industry forensic profiles, so it can detect indicators of compromise (IoC).
Through continuous monitoring, the software can also identify vulnerable software running on devices, as it compares to known lists of industry common vulnerabilities and exposures (CVE).
Threat Hunting
Advanced search capabilities and pre-built queries can simplify threat hunting. With the latest data on attacker tactics, techniques, and procedures (TTP) and IOCs, users can automate the investigation process using advanced analytics and machine learning. They can also automatically implement remediation steps to uncover, confirm, and stop hidden attack instances.
Incident Management
EDR software provides security analysts the visibility to identify infected endpoints and understand the scope of attack. It has dashboards for at-a-glance reporting that help identify incident response priorities. Forensic tools aid analysts in investigating the incident and identifying all affected applications, processes, systems, and files to pinpoint the source and method of entry.
Other important features are secure sand-boxing of infected items, analysis of behavior, correlation of new information with historical data, and automated response to quarantine files or isolate endpoints.
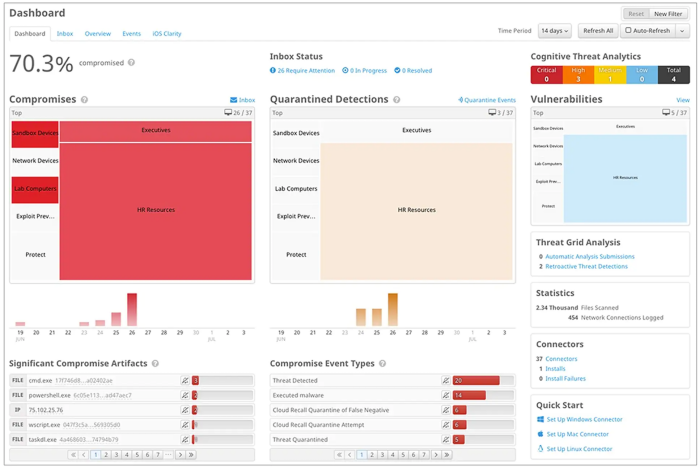
Integration
EDR software is part of a larger cybersecurity strategy. It needs to integrate easily to other security software, as well as business systems, to provide better visibility and insight to users.
Back to top
Features for Small Businesses
Small businesses need EDR software that is easy to use and ready to deploy out of the box. With fewer personnel, small companies may not be able to assign a dedicated person to man the software all the time.
- Integrated Protection: Small businesses need an EDR that can integrate with antivirus software to detect suspicious activity and block malware.
- Automated Investigation and Response: With fewer personnel, automation can streamline efforts and activities, helping users manage incidents efficiently.
- Expert Support: EDR vendors that provide regular training and assistance — especially at times when there is a high possibility of breach — are most valuable to small businesses.
Back to top
Features for Midsize Businesses
Midsize companies are often at a higher risk because of their growth and profitability. Attackers will try to put them into a difficult position, so they need to be well prepared.
- Extended Detection and Response: Midsize companies should try to look beyond standard EDR tools, looking to XDR coverage for increased protection.
- Automated Correlation and Analysis: EDR tools that can simplify the collected information and investigation process give analysts more time to respond and prevent damage.
- Automated Response: Ready-to-use scripts for different scenarios on single or multiple endpoints allow companies to stop attacks quickly, so they can focus on strengthening preventive measures.
Back to top
Features for Enterprise Businesses
Enterprises have a large attack surface because of the high number of endpoints. They need the right EDR tool to get the most value from this essential investment.
- AI-guided Detection: Large companies with thousands of endpoints need to identify the real alerts from false ones, so AI can help filter incidents and prioritize threats that need attention.
- End-to-end Visibility: With more endpoints, enterprise users need the help of interactive dashboards to make sure all points of entry are secure and functioning normally.
- Custom Remediation: Administrators may need to customize remediation steps, due to the large number and variety of possible scenarios in an enterprise incident.
 Cynet 360 is an EDR security solution for the enterprise. It provides endpoint protection and automated investigation and remediation actions — with 24/7 support from a managed detection and response (MDR) service at no additional cost. The solution uses advanced detection techniques to detect potential threats, provides full visibility, and also deploys deception technology to detect stealthy attacks.
Cynet 360 uses combined telemetry to provide visibility and protection across the entire attack surface. It natively combines and coordinates key security controls like NGAV, EDR, network traffic analysis (NTA), user behavioral analytics (UBA), and deception using various types of decoy files. It also automates investigations and incident response with pre-built and custom remediation, as well as using remediation playbooks for various attack scenarios.
Pros
Cynet 360 is an EDR security solution for the enterprise. It provides endpoint protection and automated investigation and remediation actions — with 24/7 support from a managed detection and response (MDR) service at no additional cost. The solution uses advanced detection techniques to detect potential threats, provides full visibility, and also deploys deception technology to detect stealthy attacks.
Cynet 360 uses combined telemetry to provide visibility and protection across the entire attack surface. It natively combines and coordinates key security controls like NGAV, EDR, network traffic analysis (NTA), user behavioral analytics (UBA), and deception using various types of decoy files. It also automates investigations and incident response with pre-built and custom remediation, as well as using remediation playbooks for various attack scenarios.
Pros
 CrowdSec is a free, open-source, and multi-player security solution for Linux. It is a collaborative EDR that leverages crowd power, allowing users to analyze behaviors, respond to attacks, and share signals across the community. The software can run on virtual machines, bare-metal servers, or containers.
Users can call CrowdSec from code through its API. CrowdSec shares the IP addresses of attackers across the community and enables the platform to curate and redistribute a qualified IP blacklist to all users. It decouples detection (agent) and remediation (bouncer), so it does not create a single point of failure and can fit different topologies. Written in Golang, it can parse massive amounts of logs quickly. Other features include dashboards, support for IPv4 and IPv6, and GDPR compliance.
Pros
CrowdSec is a free, open-source, and multi-player security solution for Linux. It is a collaborative EDR that leverages crowd power, allowing users to analyze behaviors, respond to attacks, and share signals across the community. The software can run on virtual machines, bare-metal servers, or containers.
Users can call CrowdSec from code through its API. CrowdSec shares the IP addresses of attackers across the community and enables the platform to curate and redistribute a qualified IP blacklist to all users. It decouples detection (agent) and remediation (bouncer), so it does not create a single point of failure and can fit different topologies. Written in Golang, it can parse massive amounts of logs quickly. Other features include dashboards, support for IPv4 and IPv6, and GDPR compliance.
Pros








