Articles
View All
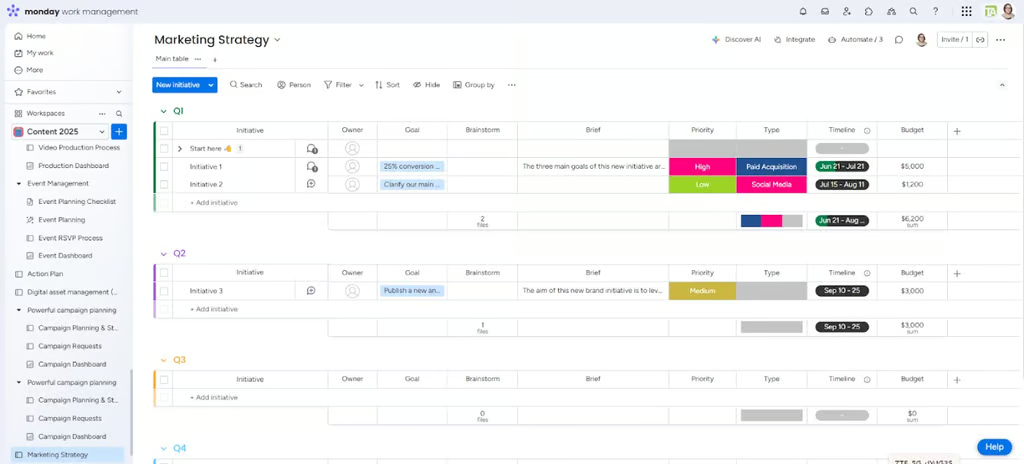
Link to 10 Best Project Management Software 

10 Best Project Management Software
The best project management software for 2025 with our expert comparison of top tools. Explore features, pricing, and the best picks for your team!
Link to Best Free Project Management Software 

Best Free Project Management Software
Discover the best free project management software, including Jira, Notion, and Trello, to manage tasks and collaborate without the cost.
Link to Best Project Management Software for Small Teams 

Best Project Management Software for Small Teams
Discover top project management software tailored for small teams to ensuring seamless collaboration and efficiency.
Link to Best Project Scheduling Software 

Best Project Scheduling Software
Planning and tracking your projects has never been easier. Check out our list of the top 5 project scheduling software and find the perfect option for your team.
Link to Best Task Management Software 

Best Task Management Software
Simplify your projects, workflow, & team. Instantly compare the best task management software & tools now!
Link to Best Agile & Scrum Project Management Software 

Best Agile & Scrum Project Management Software
Scrum is a framework for completing complex projects. Compare the Best Scrum Software & Tools for your Agile team's project management needs.
Articles
Link to What is Project Management? 

What is Project Management?
Project management is the planning & organizing of resources to achieve a specific goal. Learn about types and examples to get started.
Link to Project Management Basics: Guide for Beginners 

Project Management Basics: Guide for Beginners
Learn the basics of project management with this comprehensive guide. We'll cover everything from the planning process to daily project management tasks.
Link to 5 Phases of Project Management Life Cycle 

5 Phases of Project Management Life Cycle
Learn how to break down the project management process into five phases: Initiation, Planning, Execution, Monitoring & Control, and Closure.
Link to What is a RACI Matrix? 

What is a RACI Matrix?
Learn the best ways to use a RACI Matrix with your project to ensure that everyone understands who is responsible for what with project roles.
Link to What is Agile? 

What is Agile?
Learn what agile project management is, how it works, its real-world use, and how to deliver faster, adapt, and improve collaboration.
Link to What is the Critical Path Method? 

What is the Critical Path Method?
Learn about the Critical Path Method (CPM) in project management. Discover how it identifies key tasks and ensures timely project completion.
Articles
Link to What is Project Management? 

What is Project Management?
Learn about the best project management certifications to help you advance your career. Discover the most popular certifications, pricing, and more.
Link to PMP Certification 

PMP Certification
Learn how to get your PMP certification. We'll cover the PMP exam requirements, best practices, and tips for success.
Link to CAPM Certification 

CAPM Certification
Start your project management career journey by knowing what the CAPM certification is and how it can help you in your career. Read our guide for details.
Link to PMI-ACP Certification 

PMI-ACP Certification
Are you interested to get the PMI-ACP certification? Learn the best way in how to prepare and take the project management certification online.
Link to Google Project Management Certificate 

Google Project Management Certificate
The Google Project Management Certificate focuses on skills needed for project management. Explore this Google certification program now.
Link to Scrum Certification 

Scrum Certification
Certified Scrum Masters earn 40% higher salary on average than non-certified Scrum Masters. Check out these Scrum certifications now.
Articles
View All
Link to Project Manager Career Path 

Project Manager Career Path
Get an overview of the project manager career path, from the skills and education required to the salary, job growth, and more.
Link to How to Create a Project Management Plan in 5 Steps 

How to Create a Project Management Plan in 5 Steps
We've made an easy-to-follow guide to help you create a project management plan in X steps. Gain key insights & practical tips to ensure project success.
Link to Best Ready-to-Use Project Management Templates 

Best Ready-to-Use Project Management Templates
PMP & PMO Templates are used to initiate, execute & report. Check out this set of 50 templates now.
Link to 14 Project Management Metrics to Track to Quantify Success 

14 Project Management Metrics to Track to Quantify Success
Project management metrics, such as actual cost & ROI, help track & quantify your success. Read the full list here.
Link to How AI Is Changing Project Management: Uses, Impacts, & Trends 

How AI Is Changing Project Management: Uses, Impacts, & Trends
learn how AI is transforming project management with planning, risk management, decision-making, & team collaboration tools Explore trends & case studies.
Link to How to Write a Project Report 

How to Write a Project Report
Project managers are often tasked with producing project reports for stakeholders and leadership. Learn how to write a project report now.

-
Software Guides Link to 10 Best Project Management Software 10 Best Project Management SoftwareThe best project management software for 2025 with our expert comparison of top tools. Explore features, pricing, and the best picks for your team!Link to Best Free Project Management Software
10 Best Project Management SoftwareThe best project management software for 2025 with our expert comparison of top tools. Explore features, pricing, and the best picks for your team!Link to Best Free Project Management Software Best Free Project Management SoftwareDiscover the best free project management software, including Jira, Notion, and Trello, to manage tasks and collaborate without the cost.Link to Best Project Management Software for Small Teams
Best Free Project Management SoftwareDiscover the best free project management software, including Jira, Notion, and Trello, to manage tasks and collaborate without the cost.Link to Best Project Management Software for Small Teams Best Project Management Software for Small TeamsDiscover top project management software tailored for small teams to ensuring seamless collaboration and efficiency.Link to Best Project Scheduling Software
Best Project Management Software for Small TeamsDiscover top project management software tailored for small teams to ensuring seamless collaboration and efficiency.Link to Best Project Scheduling Software Best Project Scheduling SoftwarePlanning and tracking your projects has never been easier. Check out our list of the top 5 project scheduling software and find the perfect option for your team.Link to Best Task Management Software
Best Project Scheduling SoftwarePlanning and tracking your projects has never been easier. Check out our list of the top 5 project scheduling software and find the perfect option for your team.Link to Best Task Management Software Best Task Management SoftwareSimplify your projects, workflow, & team. Instantly compare the best task management software & tools now!Link to Best Agile & Scrum Project Management Software
Best Task Management SoftwareSimplify your projects, workflow, & team. Instantly compare the best task management software & tools now!Link to Best Agile & Scrum Project Management Software Best Agile & Scrum Project Management SoftwareScrum is a framework for completing complex projects. Compare the Best Scrum Software & Tools for your Agile team's project management needs.
Best Agile & Scrum Project Management SoftwareScrum is a framework for completing complex projects. Compare the Best Scrum Software & Tools for your Agile team's project management needs. - Project Management 101 Link to What is Project Management?
 What is Project Management?Project management is the planning & organizing of resources to achieve a specific goal. Learn about types and examples to get started.Link to Project Management Basics: Guide for Beginners
What is Project Management?Project management is the planning & organizing of resources to achieve a specific goal. Learn about types and examples to get started.Link to Project Management Basics: Guide for Beginners Project Management Basics: Guide for BeginnersLearn the basics of project management with this comprehensive guide. We'll cover everything from the planning process to daily project management tasks.Link to 5 Phases of Project Management Life Cycle
Project Management Basics: Guide for BeginnersLearn the basics of project management with this comprehensive guide. We'll cover everything from the planning process to daily project management tasks.Link to 5 Phases of Project Management Life Cycle 5 Phases of Project Management Life CycleLearn how to break down the project management process into five phases: Initiation, Planning, Execution, Monitoring & Control, and Closure.Link to What is a RACI Matrix?
5 Phases of Project Management Life CycleLearn how to break down the project management process into five phases: Initiation, Planning, Execution, Monitoring & Control, and Closure.Link to What is a RACI Matrix? What is a RACI Matrix?Learn the best ways to use a RACI Matrix with your project to ensure that everyone understands who is responsible for what with project roles.Link to What is Agile?
What is a RACI Matrix?Learn the best ways to use a RACI Matrix with your project to ensure that everyone understands who is responsible for what with project roles.Link to What is Agile? What is Agile?Learn what agile project management is, how it works, its real-world use, and how to deliver faster, adapt, and improve collaboration.Link to What is the Critical Path Method?
What is Agile?Learn what agile project management is, how it works, its real-world use, and how to deliver faster, adapt, and improve collaboration.Link to What is the Critical Path Method? What is the Critical Path Method?Learn about the Critical Path Method (CPM) in project management. Discover how it identifies key tasks and ensures timely project completion.
What is the Critical Path Method?Learn about the Critical Path Method (CPM) in project management. Discover how it identifies key tasks and ensures timely project completion. - Certifications Hub Link to What is Project Management?
 What is Project Management?Learn about the best project management certifications to help you advance your career. Discover the most popular certifications, pricing, and more.Link to PMP Certification
What is Project Management?Learn about the best project management certifications to help you advance your career. Discover the most popular certifications, pricing, and more.Link to PMP Certification PMP CertificationLearn how to get your PMP certification. We'll cover the PMP exam requirements, best practices, and tips for success.Link to CAPM Certification
PMP CertificationLearn how to get your PMP certification. We'll cover the PMP exam requirements, best practices, and tips for success.Link to CAPM Certification CAPM CertificationStart your project management career journey by knowing what the CAPM certification is and how it can help you in your career. Read our guide for details.Link to PMI-ACP Certification
CAPM CertificationStart your project management career journey by knowing what the CAPM certification is and how it can help you in your career. Read our guide for details.Link to PMI-ACP Certification PMI-ACP CertificationAre you interested to get the PMI-ACP certification? Learn the best way in how to prepare and take the project management certification online.Link to Google Project Management Certificate
PMI-ACP CertificationAre you interested to get the PMI-ACP certification? Learn the best way in how to prepare and take the project management certification online.Link to Google Project Management Certificate Google Project Management CertificateThe Google Project Management Certificate focuses on skills needed for project management. Explore this Google certification program now.Link to Scrum Certification
Google Project Management CertificateThe Google Project Management Certificate focuses on skills needed for project management. Explore this Google certification program now.Link to Scrum Certification Scrum CertificationCertified Scrum Masters earn 40% higher salary on average than non-certified Scrum Masters. Check out these Scrum certifications now.
Scrum CertificationCertified Scrum Masters earn 40% higher salary on average than non-certified Scrum Masters. Check out these Scrum certifications now. -
Tools & Resources Link to Project Manager Career Path Project Manager Career PathGet an overview of the project manager career path, from the skills and education required to the salary, job growth, and more.Link to How to Create a Project Management Plan in 5 Steps
Project Manager Career PathGet an overview of the project manager career path, from the skills and education required to the salary, job growth, and more.Link to How to Create a Project Management Plan in 5 Steps How to Create a Project Management Plan in 5 StepsWe've made an easy-to-follow guide to help you create a project management plan in X steps. Gain key insights & practical tips to ensure project success.Link to Best Ready-to-Use Project Management Templates
How to Create a Project Management Plan in 5 StepsWe've made an easy-to-follow guide to help you create a project management plan in X steps. Gain key insights & practical tips to ensure project success.Link to Best Ready-to-Use Project Management Templates Best Ready-to-Use Project Management TemplatesPMP & PMO Templates are used to initiate, execute & report. Check out this set of 50 templates now.Link to 14 Project Management Metrics to Track to Quantify Success
Best Ready-to-Use Project Management TemplatesPMP & PMO Templates are used to initiate, execute & report. Check out this set of 50 templates now.Link to 14 Project Management Metrics to Track to Quantify Success 14 Project Management Metrics to Track to Quantify SuccessProject management metrics, such as actual cost & ROI, help track & quantify your success. Read the full list here.Link to How AI Is Changing Project Management: Uses, Impacts, & Trends
14 Project Management Metrics to Track to Quantify SuccessProject management metrics, such as actual cost & ROI, help track & quantify your success. Read the full list here.Link to How AI Is Changing Project Management: Uses, Impacts, & Trends How AI Is Changing Project Management: Uses, Impacts, & Trendslearn how AI is transforming project management with planning, risk management, decision-making, & team collaboration tools Explore trends & case studies.Link to How to Write a Project Report
How AI Is Changing Project Management: Uses, Impacts, & Trendslearn how AI is transforming project management with planning, risk management, decision-making, & team collaboration tools Explore trends & case studies.Link to How to Write a Project Report How to Write a Project ReportProject managers are often tasked with producing project reports for stakeholders and leadership. Learn how to write a project report now.
How to Write a Project ReportProject managers are often tasked with producing project reports for stakeholders and leadership. Learn how to write a project report now. - Agile Agile
- Scrum Scrum
- Construction Construction
-
- Marketing Marketing